
How threat actors continuously exploit SSO weaknesses to compromise identities, critical systems, and business operations
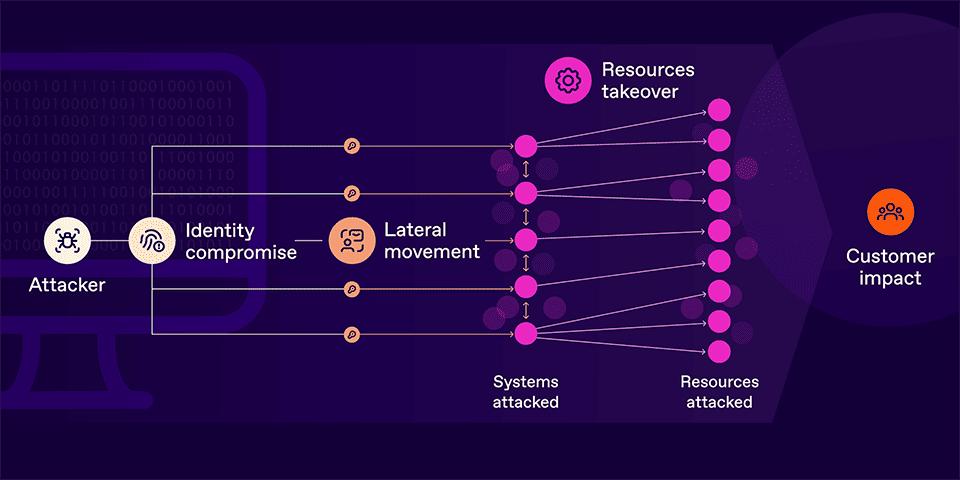
Table stakes security controls aren’t adequately protecting enterprises from breaches. Case in point, the number of data compromises jumped 78% in 2023 over a record-breaking 2022. This translates to more than 80% of organizations having suffered an identity-related breach in the last 12 months.
Attackers are, again and again, using phishing attacks, session hijacking, credential theft, and similar methods to extract a user’s login credentials. Alternatively, attackers may appear as an already authenticated user by obtaining an access token, which is often embedded in a browser cookie.
SSO isn’t detecting or stopping these credential compromises. Once attackers have bypassed SSO defenses, they can proceed to:
 Figure 01. Attackers continually compromise identities even with SSO in place. Once an identity is compromised, the threat actor will attempt to exfiltrate data and take over key resources.
Figure 01. Attackers continually compromise identities even with SSO in place. Once an identity is compromised, the threat actor will attempt to exfiltrate data and take over key resources.
At SGNL, we describe this ease of identity compromise — essentially, what makes these breaches possible — as the “Authentication Gap.” Once authentication is duped, threat actors can inflict serious damage if the compromised identity has excessive or standing access rights, a common occurrence even for companies that enforce the principle of least privilege access.
So, why is SSO not eliminating or reasonably mitigating the Authentication Gap?
While SSO platforms provide authentication features like two-factor authentication (2FA), session lifetime controls, login restrictions based on IP address or time of day, etc., this set of controls is often disjointed from the target application’s features.
Regardless of the authenticated session lifetime set at the SSO provider, the application session control is determined by the application itself. Session lifetime may be explicitly specified by the application developer, or it can be set by an application administrator managing their end-user experience. But many companies and CISOs mistakenly assume that the SSO provider directly manages sessions in the target applications.
This disconnect between SSO providers and applications plays out in several important ways:
As mentioned above, threat actors capitalize on these vulnerabilities through phishing campaigns, malware, session hijacking, and side channel attacks. Attackers have also directly compromised SSO providers.
Once the Authentication Gap is exploited, attackers gain broad access to a company’s systems and data. As a result, identity has become the new attack surface. Hence, that 80% stat we shared at the beginning.
If you do not already have a program to implement phishing-resistant authentication, explore tools that minimize the Authentication Gap. Passkeys or phishing-resistant MFA are great options, and many commercial providers make these solutions available.
For cloud services, you must implement SSO that then takes advantage of your strong authentication.
Regardless of how secure you make your company’s authentication, today’s technology mostly does not prevent session hijacking. And the threat of malicious insiders accessing unauthorized data cannot be prevented by hardening authentication alone. In addition to stronger authentication protocols, you must also fortify your access rights for effective security.
Our CTO Atul Tulshibagwale’s latest white paper provides practical steps enterprises can take to achieve stronger access security. You’ll learn how to measure the effectiveness of your own approach and access policies, along with adopting the latest, dynamic approaches to improved access security that compensate for SSO’s shortcomings. Download the white paper today.
Want more of the latest identity-first security topics and trends delivered to your inbox? Helpful and insightful content, no fluff.