
Identity events happen continuously, but siloed tools miss critical signals. SGNL’s CAEP Hub reacts to identity and security changes in real time—across IDP, EDR, IAM, HRIS, and more—to assess risk and trigger actions, enabling Continuous Identity and Zero Trust enforcement.
Gain centralized visibility and control by combining signals from multiple identity, security, and business systems.
Immediately evaluate access policies and enforce remediation actions when user risk changes.
Orchestrate multiple remediation actions like session revocation or privilege reduction when conditions shift.
Minimize the impact of breaches by actively monitoring security signals from across your environment
Quickly integrate with your existing identity, security and business applications to using the CAEP standard or proprietary APIs
Evaluate signals against fully correlated and contextual information about your human and non-human identities
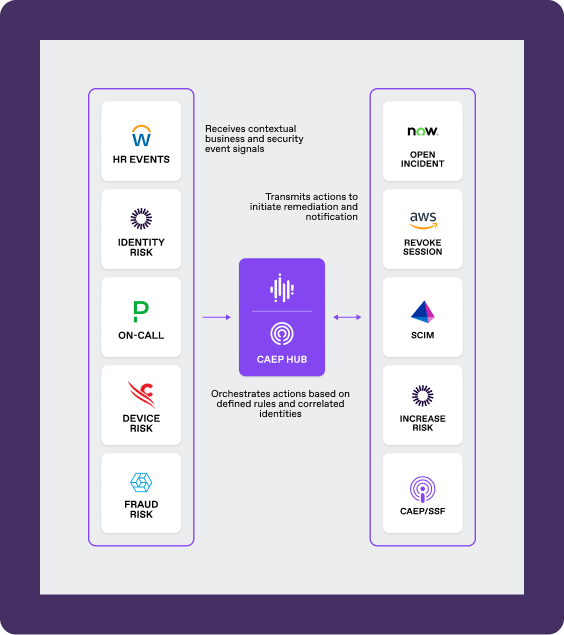
Orchestrate real-time identity events as soon as security signals exist, don’t wait to be notified by your security team
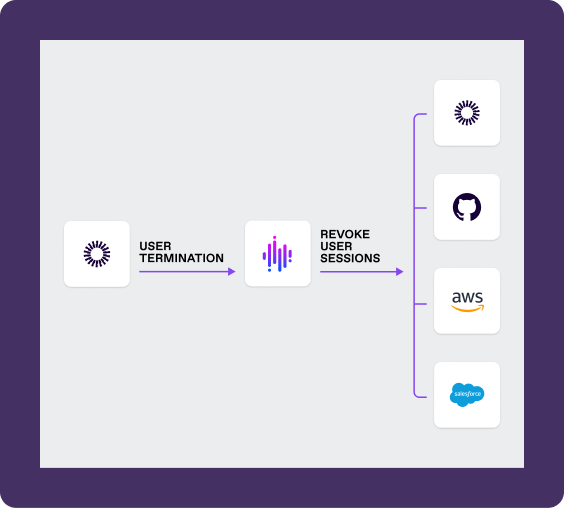
Quickly revoke sessions, initiate single-logout and remove entitlements leveraging your existing IAM tools
Automatically notify your security team or SOC systems about completed identity remediation actions
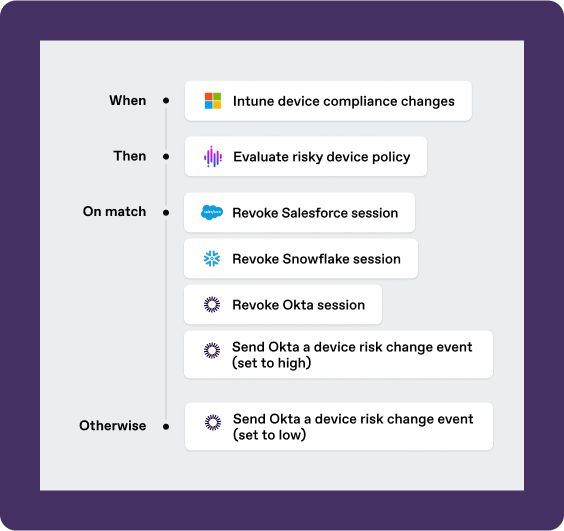
Dynamically evaluate changes and orchestrate identity actions based on contextual rules and policies
Revoke active sessions and access tokens anytime there’s a change in a user’s status
Trigger identity administration actions based on lifecycle events, such as employee hire or job change
This introductory white paper by Atul Tulshibagwale, inventor of CAEP, covers everything you need to know about CAEP and how to implement in the enterprise

Real, helpful conversations with identity leaders who know Continuous Identity
SGNL automatically responds to events happening anywhere in your ecosystem. Sessions and access across enterprise services and apps are dynamically controlled and based on your own policies. No matter what the event, SGNL’s CAEP Hub can determine and carry out the appropriate actions.
Explore our curated library of resources
Leveraging CAEP Hub to extend Microsoft’s security across all your applications
The evolution of authorization: how to achieve zero standing privileges
CAEP and Shared Signals in a nutshell
Shared Signals CAEP and RISC: real world use cases
Caep.dev demo
Moving IAM from manual response to instant breach containment with Shared Signals
Beyond the buzzwords: why JITA, not JITP, delivers true Zero Standing Privilege
The impact of device posture on identity security

SGNL helps you launch your AI initiatives safely—without opening the door to over-permissioned access.