
Eliminate standing access with high performance, context-aware policies.


In a standing access setup, a spike in the chart indicates a firefight where a user gains extra access to fix an issue, often for longer than needed, which causes risk. Zero Standing Privilege creates a much quicker return to normal.


In a Zero Standing Privilege environment, the area under the graph is zero when a user doesn’t have a session or access token, leaving no rights for threats to exploit. With standing access, some access is always available via user credentials.
SGNL’s dynamic access platform is built with a microservices-based architecture, bringing the level of scalability, performance and reliability required by enterprise customers. Coupled with our enterprise identity graph we can provide API response times of under 100ms at the 95th percentile.
Whether deployed for 500 or 500,000 users or managing 10 policies or 10,000, the SGNL platform is designed to handle the operational scale of today’s enterprise.
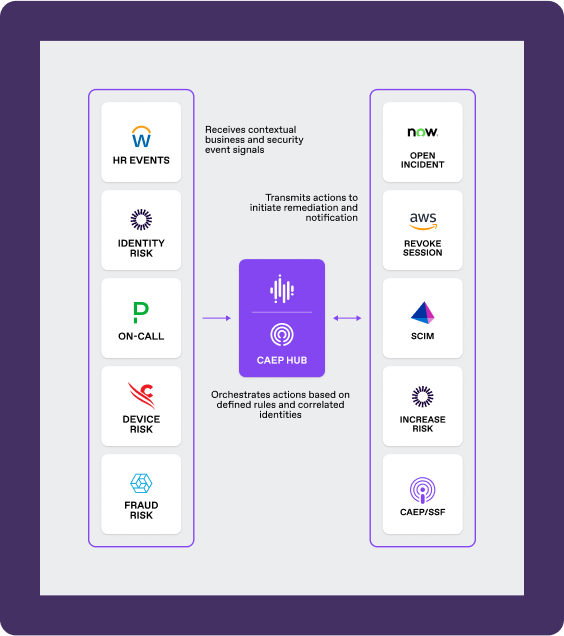
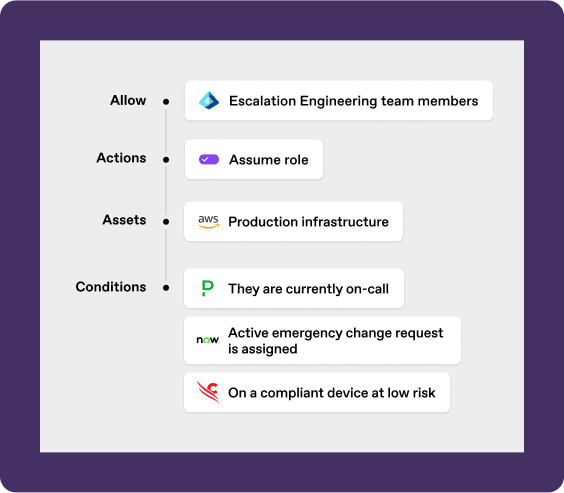
SGNL’s innovative policy management system makes it simple to reuse policies across your systems. This approach allows the application owners to build and maintain policies in a simple, human readable format while allowing identity and security teams to establish global controls and policies.
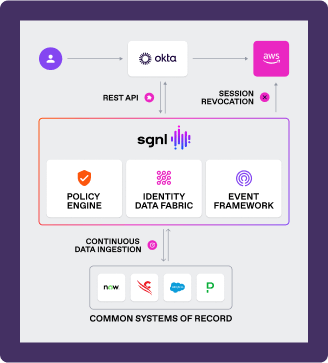
The SGNL platform is offered in two formats: A fully cloud-based, highly-available SaaS solution operating in multiple regions, or an on-prem Kubernetes appliance that can be installed in your own datacenter or cloud VPC. In either case the result is a reliable solution that you can depend on.
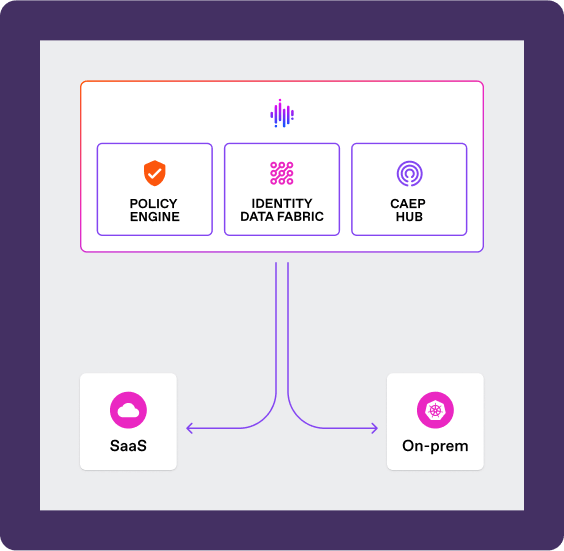
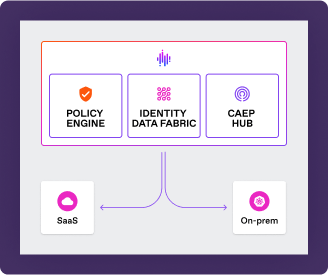
Start by approaching Zero Standing Privilege incrementally, focusing on key areas to begin with.
Build and apply reusable human readable policies across multiple services. Version control policies and run them in simulation to ensure no business disruption.
Assemble the building blocks that can be leveraged to create policies. Gain an understanding of the sources of truth that the policies depend on.
Gather insights into access request denials and approvals. Integrate with your existing SIEM for log aggregation and reporting.


See how one of the world’s largest companies protected tens of billions in annual revenue by eliminating AWS standing privileges through SGNL—shrinking attack surfaces, preventing costly errors, and maintaining compliance without sacrificing efficiency. All in less than 6 months.

Let us show you how to achieve Zero Standing Privilege using context-aware policy decisions that enforce your business rules.