
Featured guest post. Static access models can’t keep up with modern threats—learn how Continuous Identity enables dynamic, risk-aware access decisions that align with how your organization actually operates.

This is the final article of a three-part series taking a look at continuous identity. The first article introduced the concept of continuous identity and the role it can play in solving some of the fundamental issues with traditional identity management that is often built upon static assumptions, with the second taking a look at the concepts needed to build a Continuous Identity solution.
This article will focus on understanding the capabilities and pain points that can allow such a concept to be started.
The legacy approach to authorization and access enforcement was largely focused upon access control entries and lists - with the static alignment of subjects to actions - the classic “Bob as read access”, whilst “Alice has write”. The net result was excessive, static and stale permissions models. These models were initially held within applications, but the early market for external authorization products essentially moved the administration, decision making and enforcement aspects out of the protected systems. Whilst this resulted in repeatable deployment of logic and a more centralized and scalable way of designing controls, access management problems were merely transferred, not entirely resolved.
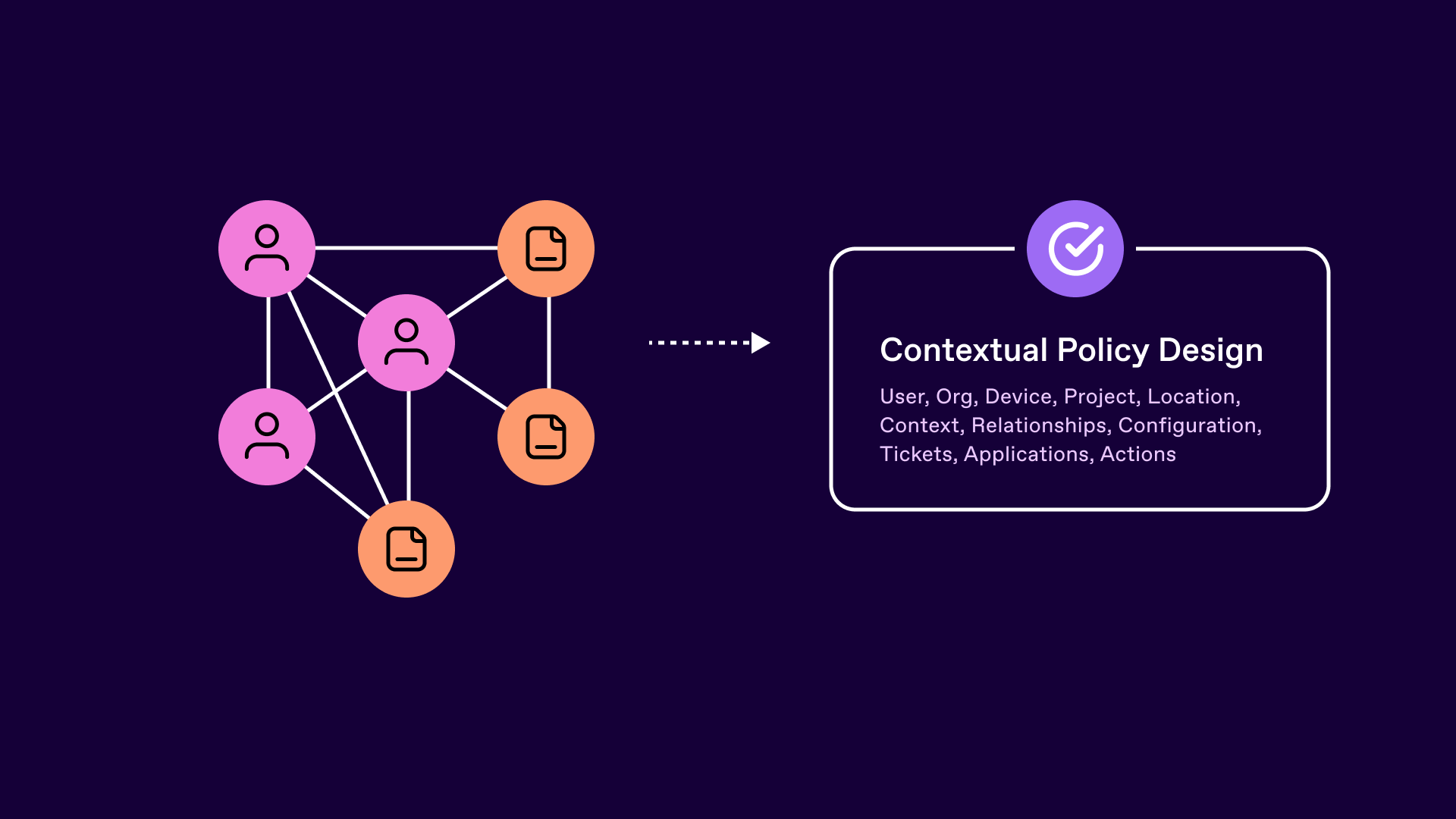
Narrow approaches to policy design and access analysis have resulted in difficulties in identifying and removing excessive permissions. An inability to view access paths holistically and account data in a relationship-focused way simply resulted in users accumulating permissions, access being copied and only coarse grained controls put in place. Widening the scope of analysis as mentioned in article 2 is a clear strategic aim of modern enterprise access management by the consumption of more identity and non-identity signals as part of the analysis equation.
However, that is only one aspect. Linear approaches to analysis do not scale or support the modern way organisations operate. Relationships and outcome based metrics drive the modern workforce and drive incentives and decision making. Access analysis in turn needs to both broaden the inclusion of these organisational data signals, but leverage them in a way that supports non-linear and graph based approaches to analysis and access decision making.
In turn this allows access policy to be more closely aligned with what the business is trying to achieve. Be that at the objective, strategy or tactics level - aligning risk and access decisions alongside changes to threat and state.
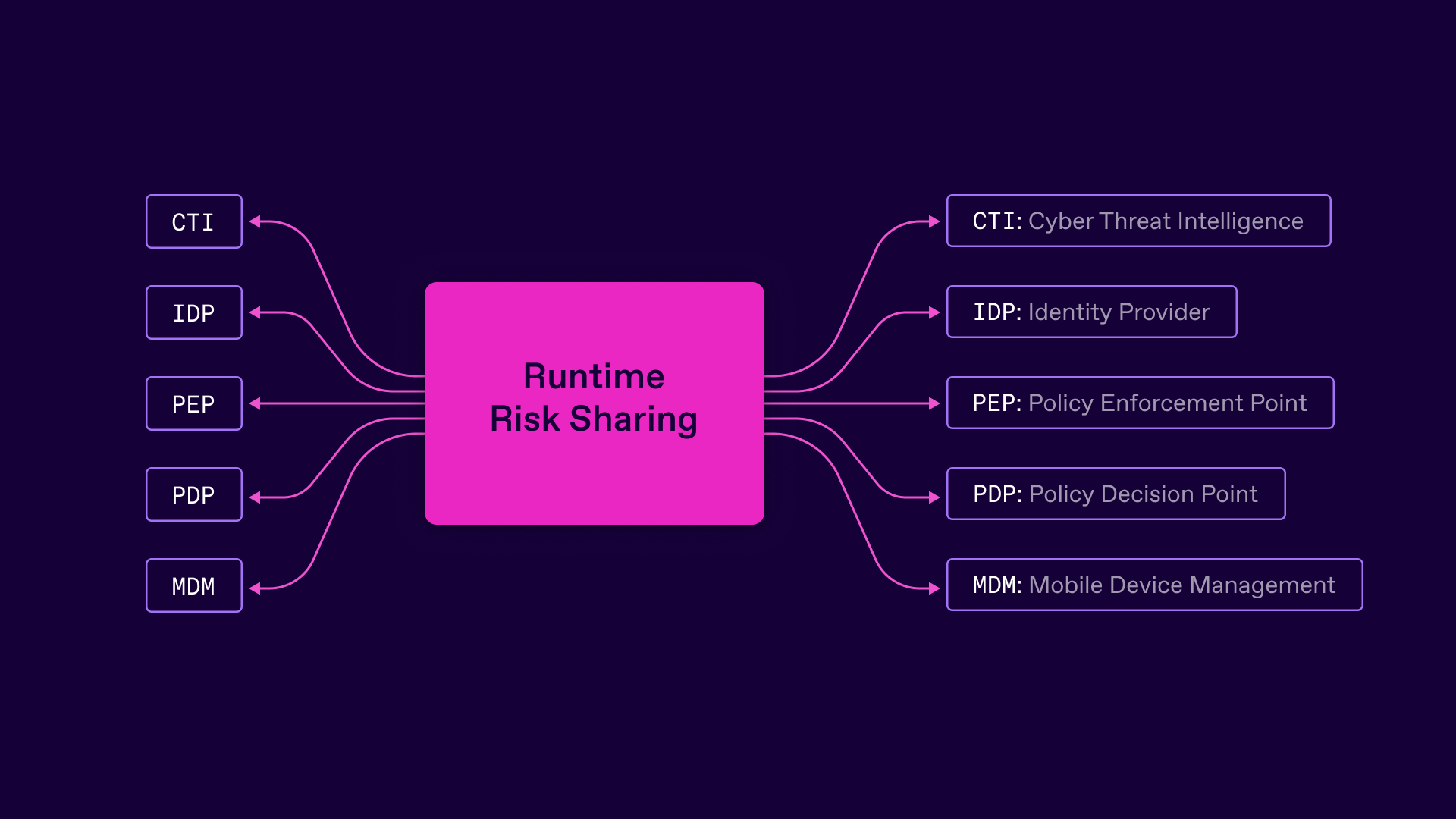
A subtle aspect of policy design and enforcement worth amplifying for the modern enterprise is the need to respond to threats dynamically.
This requires an ability to consume and act upon risk signals as and when they occur - which should not just be limited to login and authentication flows.
The Shared Signals Framework for example provides a way of integrating external events into the underlying IAM data and runtime fabric in a way that was not possible a decade ago. These micro-nudges to the control plane allow fine grained updates to be consumed (and generated) across devices, gateways and enforcement points. These signals of course are best originating from a diverse set of sources - from the corporate enterprise looking at device management, through to external threat intelligence updates and emerging vulnerabilities for software and hardware. The more diverse the data set, the more informed the decision making becomes. No one signal alone is likely to require significant response across the identity estate, but combinations are likely to occur which do require changes to live sessions, access enforcement decisions or future authentication events.
Platforms like SGNL demonstrate this approach in practice by centralizing identity and security signals into a unified fabric that can orchestrate real-time access decisions across enterprise systems—making it possible to act on these diverse signals at the speed they occur.
A dynamic and risk integrated approach to identity has significant and strategic benefits. However, there are some specific areas that can be targeted initially. Standing access - aka permissions that are pre-provisioned against an account - are one of the key contributors to things like privileged escalation and privileged abuse.
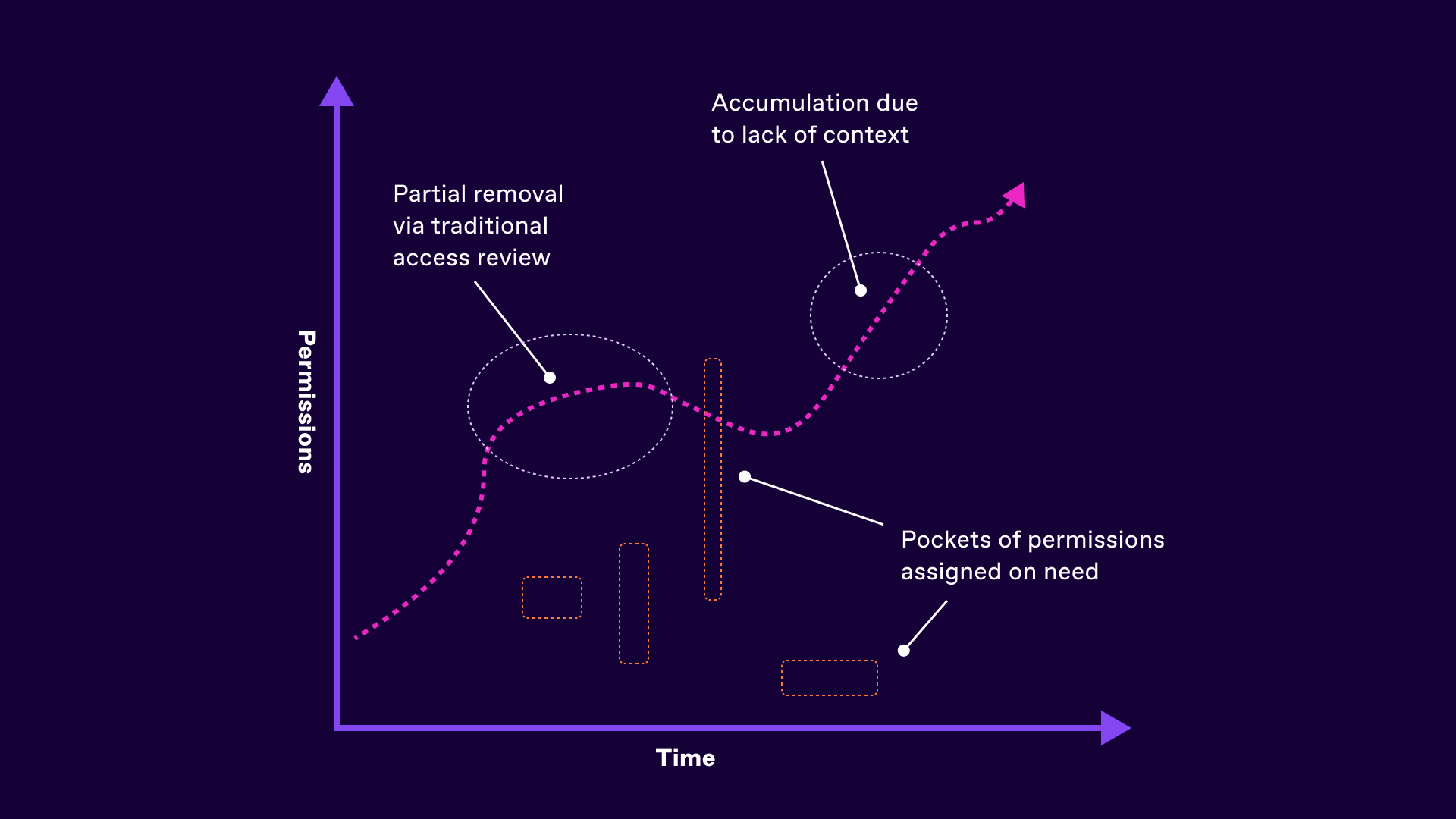
The disconnect between what is needed (and what is needed at any specific point in time) versus what is being used is a decades old issue and can be partially solved through improved access review processes.
Whilst additional context here helps line managers and application owners identify unused, overlooked and overpermissioned groups and entitlements, a migration to a zero standing model of permissions assignment makes this problem obsolete.
Strategically it is possible to reduce the length of time permissions are being assigned to individuals by focusing on task orientation and completion. Access reviews allow the new baseline to be created, which is then only actioned based on context, request approval and subsequent automatic removal either based on a set period of time or indeed when a task has completed, a service desk ticket is closed or risk level identified.
Another significant pain point to address, is the often slow and coarse grained responses that get applied during authentication and authorization enforcement events. Step-up authentication for any “high risk” login activity or transaction processing is quite well understood and at times a useful counterpoint. Whilst this is useful to manage the authentication assurance level (AAL) this is also subtly distinct from whether that user should be performing a particular action.
In addition, not all events carry the same level of risk. Whilst step-up, log-out and lock events are still required, their use can be reduced, end user experience improved and risk remediation become more targeted. Controls such as increased monitoring, risk tagging and session restriction (either via reducing the length or permissions associated with it) can often be applied without inhibiting the end user experience significantly.
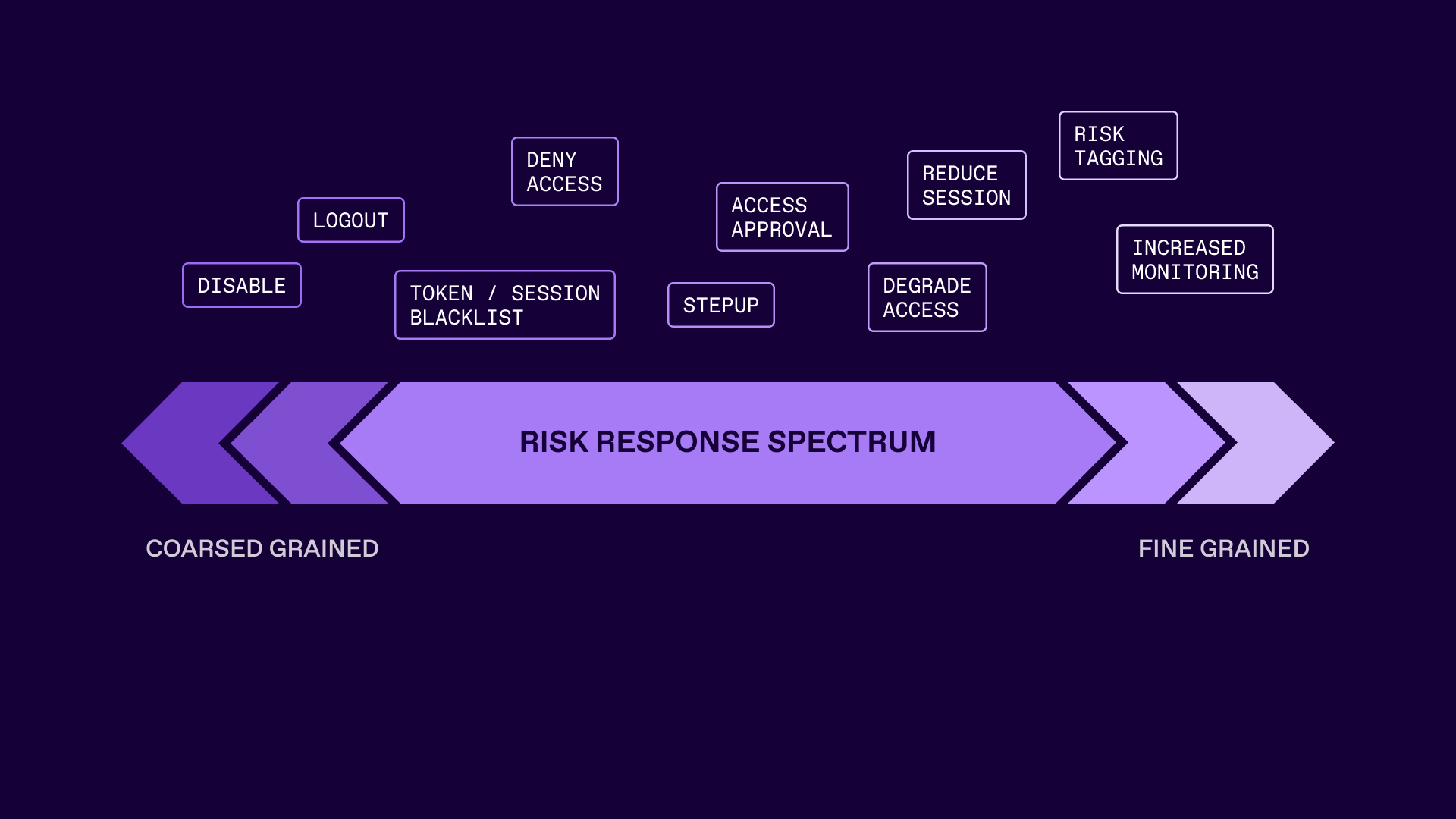
More intermediate controls such as access degradation - changing access from read and write to read-only as the end user is on a high risk device - supports both security control and improved end user happiness and task completion. Reduced calls to overworked help desk staff, improvements in staff productivity and task completion can all be achieved, in line with risk reduction and improved security posture. The security theatre often associated with step-up authentication and needless interruptive approval workflows, can be replaced with targeted risk response.
Strategic changes to the identity data and runtime fabric do not happen overnight - nor with just a technology change. It requires a closer alignment of business and cyber threat response objectives along with the benefits associated with a more integrated and responsive identity fabric. Those benefits need to be measured and communicated effectively to a broader range of stakeholders than previously. The use and augmentation of existing identity and non-identity sources is important in order to leverage inflight returns on investment from core pillars such as privileged access management, identity governance and administration and strong authentication providers. Targeted adoption against specific systems, user groups and risk areas is also key to gaining success criteria and being able to accumulate business cases and stakeholder buyin.
Solutions in this space—such as SGNL’s Identity Data Fabric and CAEP Hub—exemplify how organizations can unify existing IAM data sources and orchestrate dynamic access responses without replacing their current infrastructure investments. The key is finding an approach that connects what you already have rather than forcing wholesale replacement.
As the importance of identity to support productivity, revenue and risk reduction increases, the ability for it to become fully dynamic and responsive to external change becomes increasingly important.
Simon Moffatt has nearly 25 years experience in IAM, cyber and identity security. He is founder of The Cyber Hut - a specialist research and advisory firm based out of the UK. He is author of CIAM Design Fundamentals and IAM at 2035: A Future Guide to Identity Security. He is a Fellow of the Chartered Institute of Information Security, a regular keynote speaker and a strategic advisor to entities in the public and private sectors.