
Continuous Identity brings live context to code. Because protecting what you build should be as dynamic as the code itself.
What qualifies a user to merge code into a repository or start a CI/CD workflow? Do the when, why, and conditions matter? Repository permissions and branch protections are a starting point, but they lack the intelligence to verify authorization against company policy. They can’t check for an approved Jira ticket related to the merge, or validate that the device meets compliance standards. What should truly determine user authorization for these actions?
SGNL changes that equation by bringing Continuous Identity to the development pipeline, where policy meets process and context defines trust.
Traditional repository access controls look at static attributes: user groups, branch rules, or token scopes. But those rules can’t evaluate the real business or security context behind each change.
SGNL’s Policy Engine introduces real-time decisioning to your CI/CD pipelines and code repositories. Each access request is evaluated through a combination of:
That last element—the condition—is where SGNL adds power. It draws from the Identity Data Fabric, linking context across systems that normally operate in isolation.
Every organization stores identity information across silos, including directory services, ticketing tools, risk engines, and endpoint management systems. SGNL’s Identity Data Fabric weaves those sources together into a single, query-ready model that represents each human and non-human actor across systems. These “blended entities” let policies understand the full picture of who’s taking an action, what’s being accessed, and whether conditions still meet the organization’s security posture.
Because the Identity Data Fabric establishes relationships during data ingestion, policy decisions can happen in real time without performance trade-offs. It allows organizations to combine role-based, attribute-based, and relationship-based logic into a single decision flow, enabling enforcement that adapts as conditions change.
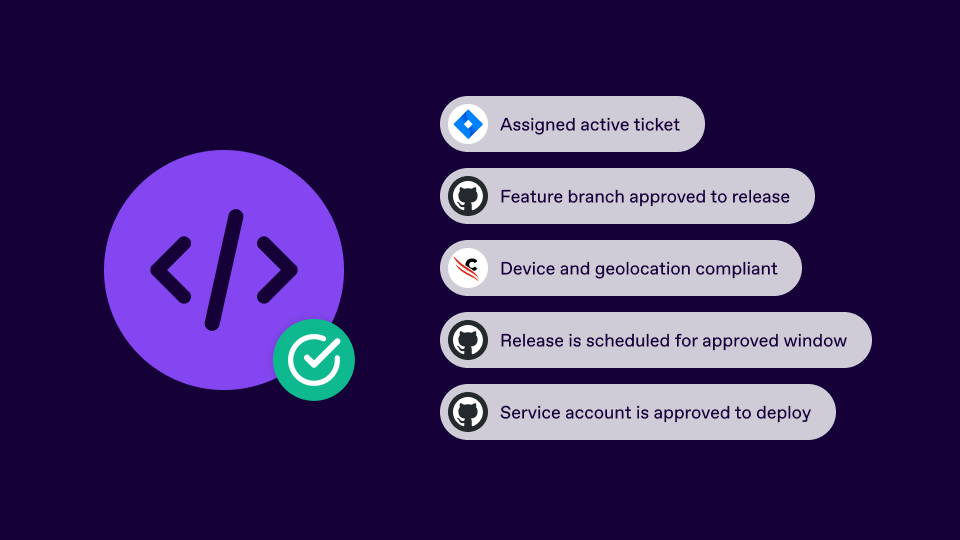
Imagine an engineer opening a pull request to merge a feature branch into the main repository. SGNL evaluates the entire situation before allowing the merge. It confirms that the developer is associated with an active and approved ticket, that the change falls within the authorized release window, and that the device used is compliant and consistent with expected behavior. If everything checks out, the merge proceeds automatically. If not, the pipeline halts. No manual review is required and there is no risk of unverified code reaching production.
SGNL checks:
That’s the difference between “allow if in the right GitHub team” and “allow if all conditions match real-time intent.”
The difference is subtle but significant: instead of trusting static permissions that assume the right context, SGNL verifies that context continuously. The result is deployment integrity that reflects live business and security intent rather than historical configuration.
Code repositories sit at the crossroads of business velocity and privileged access. A single unverified commit can open a door to sensitive systems or intellectual property. Static permissions were never designed to manage that level of risk. SGNL’s Continuous Identity approach eliminates blind spots by evaluating every code-related action in real time. Access is continuously justified.
For developers, that enforcement happens silently in the background. They continue to work in familiar tools while SGNL ensures each change aligns with policy. When context shifts thanks to an expired approval, an out-of-compliance device, or a change in on-call status, SGNL adjusts access automatically. Security becomes continuous, not conditional.
Designing effective code policies starts with a shift in mindset. Instead of granting access based on static roles or repository membership, think about what real-world conditions define “safe” access. Does the developer have an approved change ticket? Are they actively on call? Is their device healthy and known? Are they working within an approved deployment window?
These are the kinds of context that SGNL brings into every decision through the Identity Data Fabric. Each becomes part of a living policy that updates in real time as circumstances change. The result is a system where deployment pipelines are gated by live intent, not just static configuration.
A global media company uses SGNL to gate its deployment pipeline. Engineers can only push production changes when they’re actively on-call in PagerDuty, using a compliant device verified by CrowdStrike, and working from approved locations. The moment one of those conditions changes, SGNL halts the pipeline and revokes temporary credentials automatically, without manual oversight.