
Featured guest post.

This is the second of a three-part series taking a look at continuous identity. The first article introduced the concept of continuous identity and the role it can play in solving some of the fundamental issues with traditional identity management that is often built upon static assumptions.
Prior models for what we called B2E identity and access management infrastructure were quite rightly focused on people - primarily permanent staff from that people bucket, with secondary workflows and processes targeting contractors and temporary workers. The modern enterprise of course contains a more varied set of identities including different people-centric types such as business partners and joint venture users across different operational boundaries as well as more non-human focused identities that handle service to service interactions and workloads. Any modern overlay capability today needs to support a variety of identity types across this new landscape.
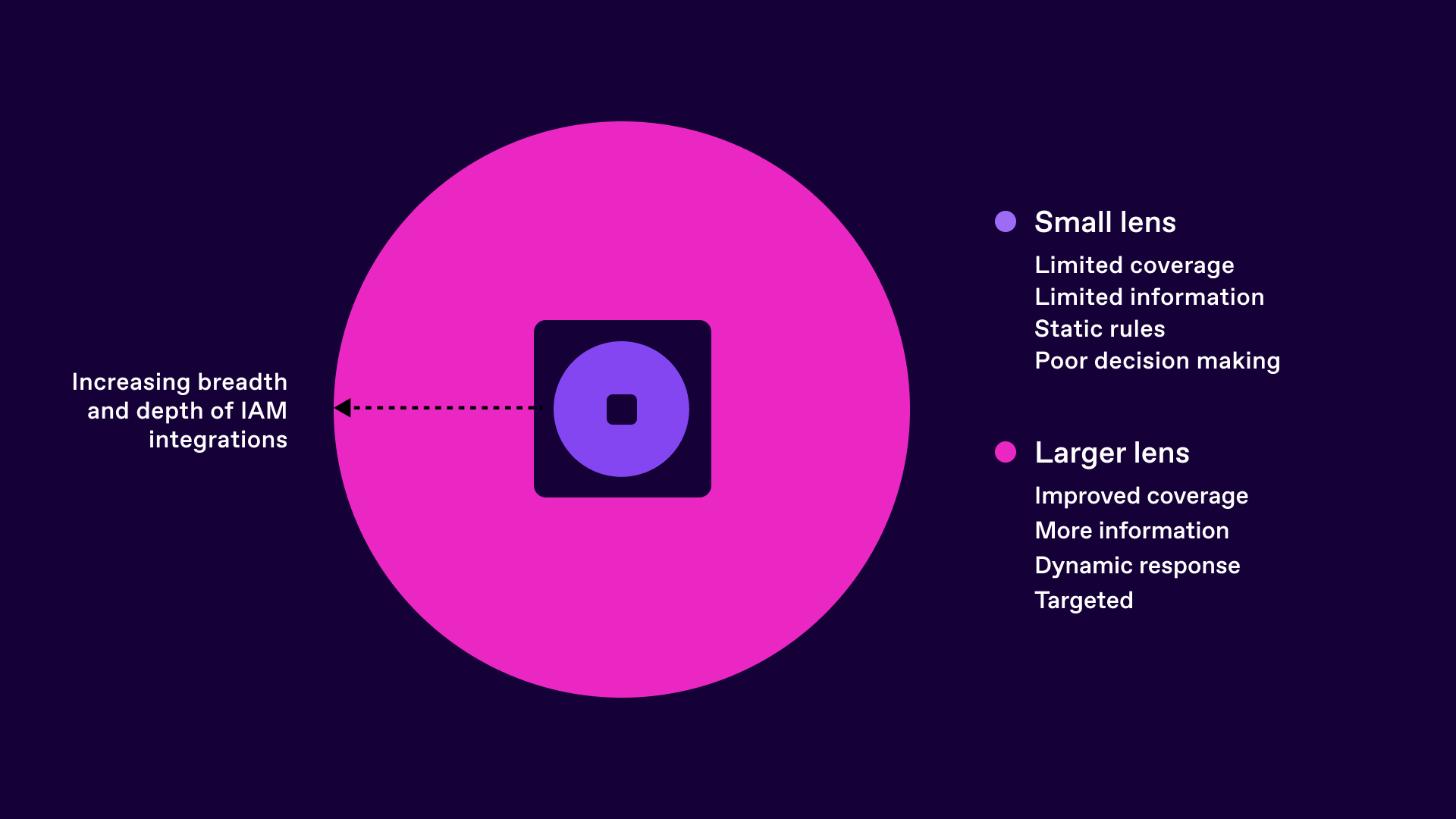
But what capabilities are needed? IAM contains many decision blind spots and information asymmetries.
Features such as identity onboarding, access request, access review management and access removal pipelines are often plagued with poor connectivity issues and a lack of context that can make informed decisions difficult. Twenty years ago the number of systems connected to an identity governance platform for example, may represent only 10% of all applications. Perhaps due to the complexity of creating connectors, the scope of compliance requirements or the effort involved in onboarding these applications, the focus was small. The associated access request and access review processes were also plagued with being of small focus.
Access request workflows often relied upon supplying a “model user” - an existing user whose access was simply to be copied verbatim onto the new user requesting access. There were no other ways to articulate what was needed, other than pointing at a colleague and saying “just like them please”. It was essentially like going to a restaurant that contained no menus - with no online reviews either. Ordering of food was to be made by sight only.
Access review and removal processes were also plagued with limited visibility with equally limited information flows. Line manager approvers or application owners had no real way of knowing exactly what a business role named “senior_mgr_bus_ops_h11” really meant, or what AD group “finance_required_g-drive” gave access to. The result? End users requested everything, and nothing was ever removed during access review and certification processes.
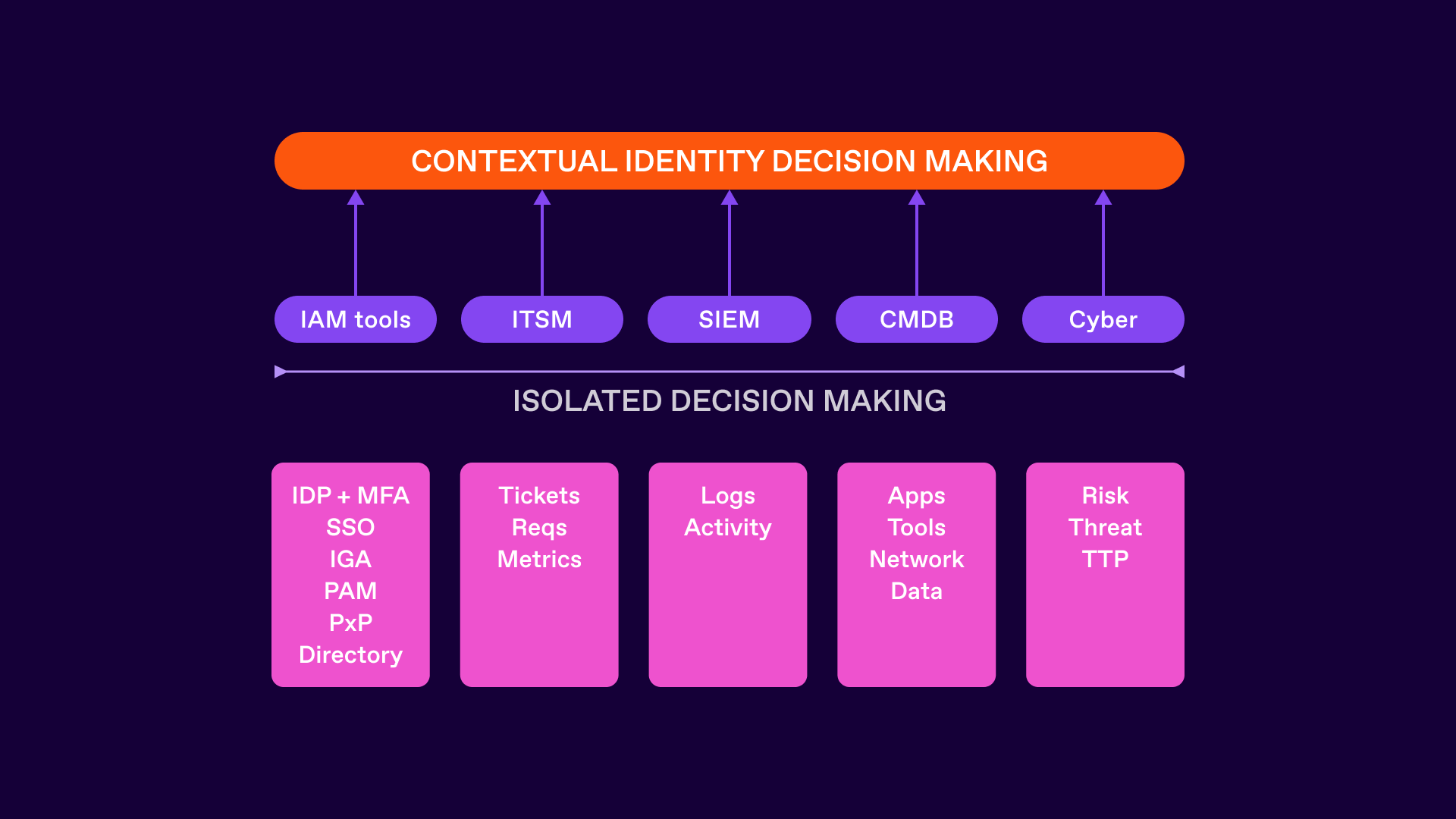
The movement towards a more contextual model of identity decision making needs to include more systems, which in turn can contribute to having more accurate information about who someone is, what they’re doing and why they’re doing it - all of which should be wrapped in a solid understanding of the changing business world.
IAM is a business-centric function, and the “business” relies upon an almost intangible set of technological, people and process related constructs to make it operate. So we need to be both broad and deep with respect to information collection as well as being flexible as to what is collected. Understanding the application landscape may well require information from a configuration management database for example. Or by understanding the current state of cyber threat intelligence can help empower session management risk analysis. Activity logging information from downstream systems becomes invaluable if trying to map access assignment and access usage information together in order to determine which groups should be removed from a user.
So we need to consider all parts of the identity lifecycle from onboarding to usage and removal, but also an orthogonal set of signals that can help improve knowledge, decision and remediation activities. Only then can we develop augmented services that overlay this complex fabric of information to start to provide a more informed, responsive and “continually” on identity service.
So what does a more contextual identity decision making model achieve? By simply improving the asymmetric information problem we can instantly start to be more targeted with respect to risk analysis and treatment. Not all identity risk is the same and a major concern for many organisations is they treat all identity related issues with the same level of priority - simply as they do not have the information to make more informed decisions. As organisations also struggle with alert-fatigue within the retrospective and reactive security operations world, being both proactive and focused immediately improves an organisation’s identity risk posture with appropriate identification and treatment options.
A simple example is the ability for the identity infrastructure to be continuously adaptive - be that cyber threat related or business process related and in turn align the IAM data and runtime services to the correct risk acceptance level. Say a user has already been enrolled, assigned the correct permissions and performed a strong authentication event at an identity provider. All of those micro-stages have (at the time they were performed) adhered to the necessary policies that may have existed. But changes happen. Perhaps the device the user performed the strong authentication from has a new operating system vulnerability found on it. The ability to treat that increased level of risk often occurs long after the trigger. At the next authentication event. At the next policy check. At the next device upgrade. All of which are often too late.
The ability to receive a risk signal from a broad non-IAM basis is only one part of the equation. What happens next? The ability to respond to external risk signals dynamically at runtime provides organizations with a strong foundation to interrupt the identity attack lifecycle - ideally before an attack has completed and has resulted in data exfiltration or more. This could include something subtle like the downgrade of a session, alteration of permissions or an entire logout and lock response. Not all external threats carry the same risk, so in turn the response should also be of a high-fidelity - fine-grained, appropriate and timely. Impacts to the end user experience should be minimised inline with the associated risk.
For example, logging out and locking all accounts, whilst “secure” may simply transfer risk to a poorly managed unlock and reset flow to an already overworked helpdesk - whilst also damaging user effectiveness and satisfaction.
As organisations see IAM move to being a strategic fulcrum within their productivity, zero trust and technology enablement plan, we need to be able to provide a more end-to-end protection model for all of our identity types, lifecycle features and capabilities.
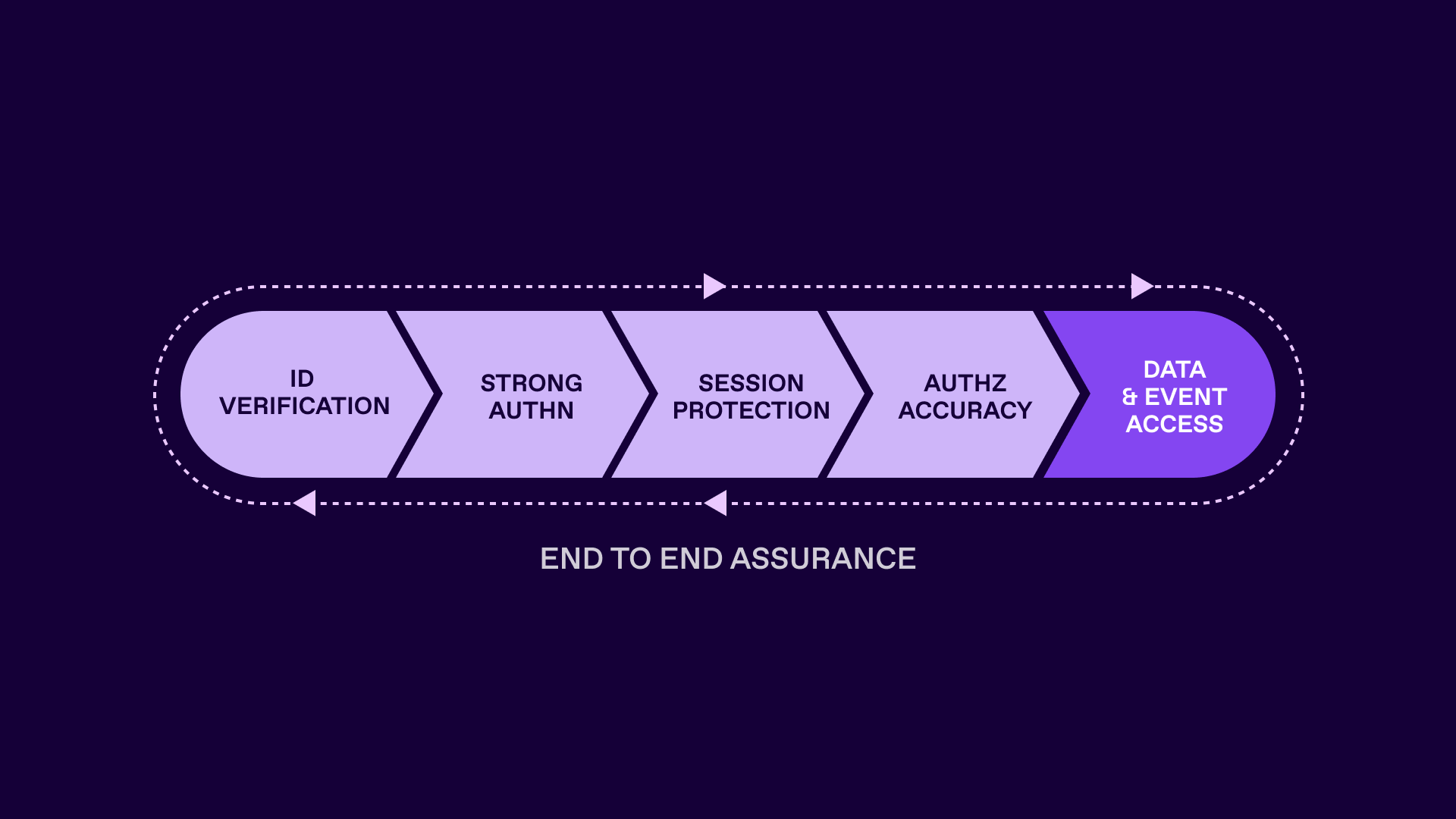
This will cover not just the identity data aspect (profiles, permissions and associated policies) but what happens post authentication - namely session management, access control decision making and enforcement. We can then start to consider assurance being a more end to end construct, instead of one that is often isolated and siloed at the identity verification and validation (IDV) and authentication stages.
The ability to impact post-authentication processing and management of sessions improves security response. The ability to improve permissions associations will support a migration towards zero standing privileges and just-in-time access that again is routed in business need and also risk tolerance. Rightsizing permissions, roles and groups has been a multi-decade-old concern for many organizations, yet the benefits impact both the productivity of end user requests and the approvers, as well risk posture.
Ultimately we can start to deliver access to data and the processing of events with realtime assurance that is inline with the current and ever changing risk associated with the identity.
Simon Moffatt has nearly 25 years experience in IAM, cyber and identity security. He is founder of The Cyber Hut - a specialist research and advisory firm based out of the UK. He is author of CIAM Design Fundamentals and IAM at 2035: A Future Guide to Identity Security. He is a Fellow of the Chartered Institute of Information Security, a regular keynote speaker and a strategic advisor to entities in the public and private sectors.
Want more of the latest identity-first security topics and trends delivered to your inbox? Helpful and insightful content, no fluff.