Every cloud provider has its own way of gating access. Roles, permission sets, federation rules, they’re all meant to keep sensitive systems safe. But without context, they leave dangerous gaps. SGNL’s Continuous Identity approach closes those gaps by enforcing policies that adapt in real time to business and security signals.
Building policies with context
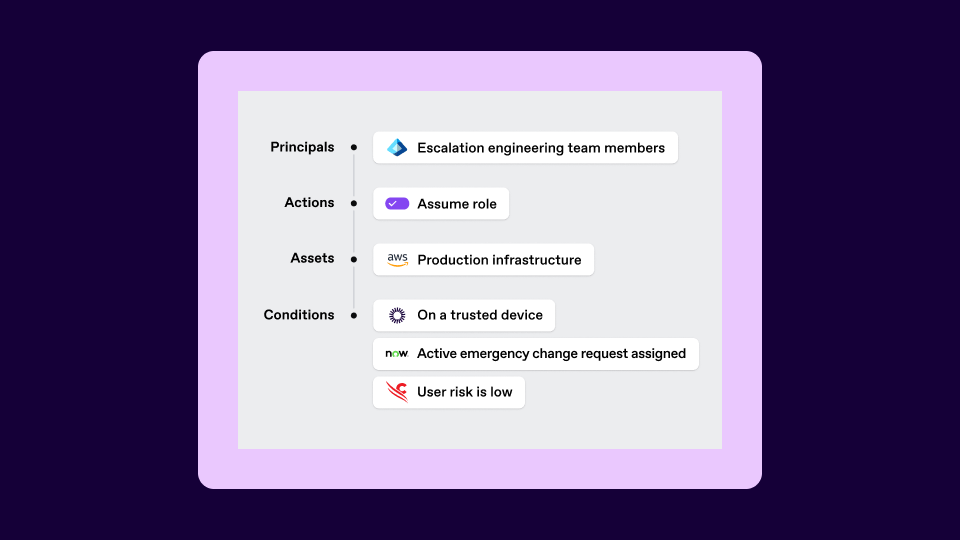
At the core of SGNL’s Policy Engine are four components:
- Principal: Who’s requesting access
- Action and access: What they’re trying to do
- Asset: The resource in question
- Condition: The live context that determines whether access should be allowed
That last piece —condition— is what makes SGNL different. Traditional entitlements or group memberships can only answer part of the question. By incorporating live context, SGNL ensures that access decisions reflect what’s actually happening in the moment. That might mean checking whether a ServiceNow ticket is still active, confirming that a device is compliant with CrowdStrike or Intune, or verifying a user’s membership across multiple directories at once.
From snippets to policies
Rather than forcing teams to start from scratch, SGNL uses reusable policy snippets that serve as building blocks. These snippets are created in a no-code interface, so IAM teams and application owners can work together without depending on developers to hard-code every change. A snippet might capture a common requirement—like “device compliant,” “ticket approved,” or “quarter-end only”—and once it’s defined, it can be dropped into any policy across the environment. The result is a policy library that’s flexible, consistent, and easy to maintain, with guardrails that prevent accidental over-permissiveness.
AWS login with a non-compliant device
An engineer gets paged in the middle of the night to fix a production issue. They open their laptop, log into AWS, and request access to a role that normally gives them admin-level visibility.
Here’s what happens next:
- SGNL checks their identity in Okta and confirms they’re on the right team.
- It sees their ServiceNow incident ticket is active and assigned.
- But CrowdStrike flags the laptop as out of compliance.
Because the device isn’t trusted, SGNL denies the request, despite the correct role and ticket. The engineer can’t use the AWS role until the device is secured.
Instead of leaving the door open for an attacker who might be using compromised credentials, SGNL enforces the fail-safe: no compliant device, no access.
Making cloud access smarter
Cloud providers each have their own mechanisms for granting access, and SGNL adapts to them rather than forcing a one-size-fits-all approach. In AWS, for example, federation assigns roles at login. SGNL strengthens this by validating tags from the identity provider, so even if a permission set has been assigned, it won’t work unless the tag requirement is met. In other environments, roles may be granted through a ServiceNow catalog or even a custom role/permission management system. SGNL operates as an authorization layer above these assignments that allows utilization of these assignments only when business and security contexts align.
Principles behind the policies
Every SGNL policy is guided by the same principles. Access is never unconditional; it must always be tied to business context. Permissions are narrowly scoped to the immediate task, enforcing least privilege through time-bound, ephemeral access. When context changes or something goes awry —say, a device falls out of compliance or a security tool raises an alert— SGNL enforces a fail-safe. Deny policies act as a veto, instantly overriding any other rules until the risk is resolved.
Why it matters
Cloud access policies aren’t just administrative checkboxes; they’re front-line defenses. Without live context, they lag behind reality, leaving exposure windows for attackers to exploit. SGNL eliminates those gaps by enforcing Continuous Identity through its real-time Policy Engine and identity action orchestration within CAEP Hub. When context changes —say a device falls out of compliance or a ticket closes— CAEP Hub acts immediately, revoking sessions, deprovisioning privileges, or triggering incident response. Access adapts in real time, grounded in reason and context rather than static assumptions.
Want to see more? Ask us how you can improve your cloud security posture. Book 15 minutes in our Expert Hours. No slides. No sales pitch. Just straight answers.