
Featured guest post. Traditional IAM was built for a static world that no longer exists—discover why point-in-time identity decisions can’t keep pace with today’s dynamic business environment and evolving cyber threats.

This is the first of a three-part series taking a look at Continuous Identity. Identities, accounts and the numerous events and triggers that influence chance upon them are not static. As employees we rarely have the same day twice. Our reporting lines are blurred and fragmented. Our responsibilities vary - but perhaps our pay stays the same! Yet, the IAM fabric and the capabilities needed to manage the identity data ecosystem is often not dynamic. It is often designed with one-time events in mind - from complex onboarding with convoluted verification and validation, to strong authentication step-up events, with the often inevitable poor user experience. IAM process can often be fragile and static in both design and implementation - a little like a one-way ratchet that adds, but rarely changes or removes. Strong identity assurance checks during onboarding are only useful for as long as that associated data is “fresh” with the assumption of no external change. That assured identity data is often also not always used in downstream systems or not profiltered correctly via provisioning. This results in duplications, inaccuracies and errors.
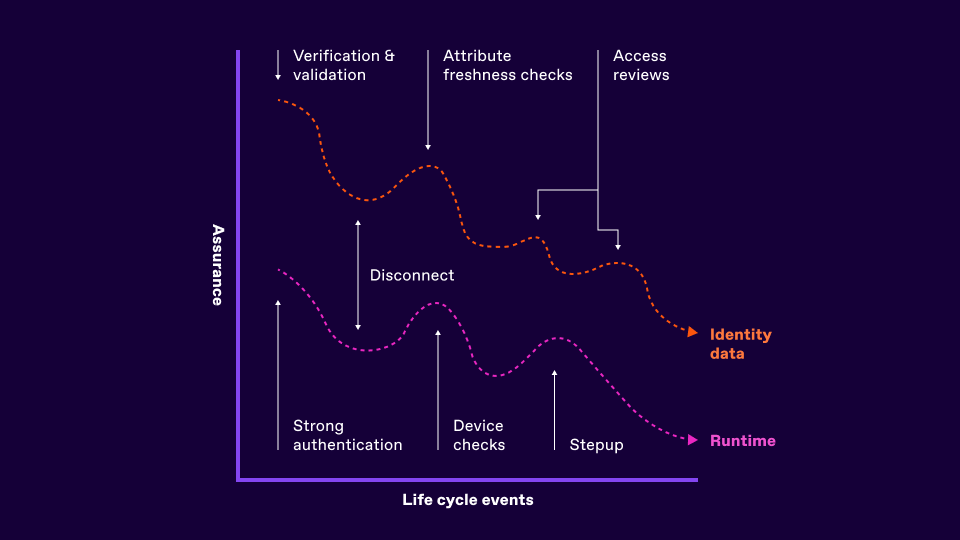
Periodic checks for the freshness of captured identity data can help - such as name changes, contact details and so on - and the obligation to perform quarterly or yearly access reviews for staff can give the illusion of data quality checks.
They are of course, lacking context, performed by non-technical stakeholders who can rush the process, afraid to remove access in case of the impact on productivity.
From a runtime usage perspective, we again leverage assurance levels during authentication - often seeing a high degree of confidence just after a login event - but that can quickly diminish over a short period of time due to a lack of device binding, long session lengths and so on. Step-up authentication is often triggered, but again can be point-in-time based on an arbitrary event. Similarly authorization enforcement and decision making steps are often singular in nature - either due to a lack of detailed context, latency or a combination of both.
A final point to consider is often seen with the disconnect of identity data that handles attributes, permission and policy information and the runtime authentication and authorization events. Both internal and external adversarial activity exploits this vulnerability daily - with insider threat, impersonation, fraud and intellectual property theft attacks common.
Simply put, the joiner-mover-leaver process was not designed to support assurance and security from the offset. It was designed to improve productivity and reduce costs - with compliance being an optional add-on to rectify market failures for those in regulated industries.
Today many mid-to-large enterprises will have numerous identity platform components. Some from the same vendor, many others a patchwork quilt of isolated legacy suppliers. Even with deployments of multiple IDPs, MFA, IGA and PAM data breaches are common. Systems are often isolated with a lack of interoperability at both the data and runtime layers with security controls that are implemented at a point in time and lack context. The end result is ultimately low assurance services at both the data and runtime layers of our IAM infrastructure.
Many organizations now have to contend with relatively static IAM data and runtime fabrics that are not keeping pace with the change often felt by the identities, accounts, tasks and events associated with them. Does this matter? Why is change so important? Most organizations are reliant upon a broad and ever-changing set of collaborations, joint ventures and partnerships, alongside a vast and often opaque supply chain of people and services. Not only does this introduce an increased volume of identities and relying systems to manage, it introduces different types of identities - including non-human, agentic-AI and infrastructure related.
We also need to consider a more hybrid deployment landscape - from on-premises, to cloud-native, PaaS and SaaS. Operationally the IAM control plane has to integrate with more systems and deliver more functionality. If everything stayed the same, that in itself would represent a large change in functional and non-functional requirements, metrics and stakeholders.
Unfortunately that is not all. The modern enterprise faces increasing levels of uncertainty. From geopolitics, trade and challenger startups, to hiring issues, employee fraud and an ever evolving set of external cyber threats that are becoming increasingly automated, complex to detect and difficult to recover from.
As IAM moves from being a tactical component with ever-decreasing budget and operating in a reactionary vacuum, it has become a strategic fulcrum that empowers productivity improvements, risk reduction and revenue generation by allowing the business to be more agile and competitive.
But for that to take place, the IAM infrastructure needs to modernize - and be able to identify, analyse and respond to a range of events from both technical and business stakeholders.
Orthogonal technical platforms now rely upon identity working effectively or are integrating directly against various identity-related components.
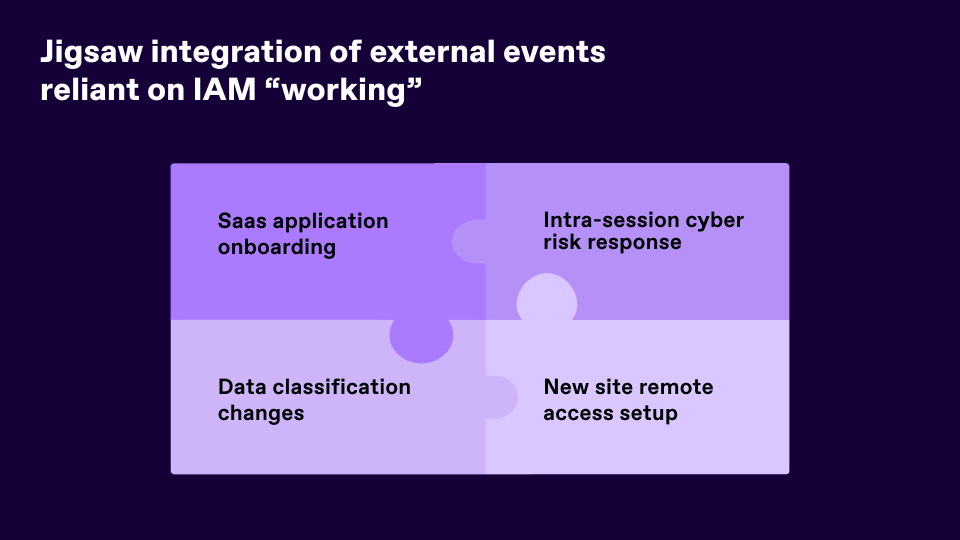
Network, SASE, endpoint and data security tools assume the identity layer can self-discover, react to data and contextual changes, onboard new systems rapidly and be event driven. Onboarding a new SaaS application should not be slowed down by poor IAM. Cyber threat detection should not have the recovery stage impacted by poor IAM. Changes to data classification tags should be accessible immediately and not be reliant upon hours or days worth of IAM changes.
More and more systems are reliant upon and make assumptions about the underlying IAM data layer - including identities, accounts, permissions and policies. Those systems will not wait for a session to end (3 days), a service ticket to be created and fulfilled (3 weeks) or a connector to be built (3 months). If the underlying IAM data is not hygienic and responsive, it will be circumvented, resulting in more disconnection and isolation.
Due to the broader integration and increased importance of identity, the impact of getting it “wrong” is considerable. The impact on productivity, security and business agility increases and becomes tangible - impacting metrics across a range of systems and stakeholders. The broader integration exposes the IAM fabric to more change, which continually alters the risk posture of the identity components.
The assurance of a created identity, or the risk associated with an assigned permission will vary - simply based on integration, usage and the threat model associated with those components at any moment in time. Many organisations struggle with being able to put the identity fabric in the lens of risk analysis, resulting in poorly selected security controls or plausible deniability associated with the risk and likelihood of specific threats.
As the business environment becomes more strategically reliant on IAM, the risks associated with external cyber threats, competitive challenges and non-compliance are exposed to the identity data and identity life cycles under pinning it. To that end, IAM needs to become not just reactive to these external events, but more aligned and in turn strategically able to shift to a preventative position when it comes to risk reduction or mitigation.
This will require the IAM fabric to use more information about its surroundings - by integrating with a broader array of business systems to help identify assets, systems, and the reasoning behind identity related requests. This could include access request and ticketing systems, configuration management tools or risk management platforms.
More identities, more types of identities and the associated policies and permissions should move under management, alongside improved signalling with respect to both previous and current high risk events. Events associated with previously assigned permissions, or threat intelligence data with respect to devices or locations should be integrated and easily propagated to the IAM components.
Ultimately organizations should be able to proactively make changes to identities, permissions and policy before there is a cascading impact on integrated systems. This move to a more proactive stance is both critical and conceptual difference to how IAM was statically managed in the past. This view of “Continuous Identity” aligns more closely with how the modern enterprise is now operating - which is “always on” and continually receptive to both internal and external events that impact strategic business decision making.
Moving IAM from being rooted in a “waterfall” methodology to one that is more integrated and proactive supports the vision of identity being an enabling technology, that is composable and able to rightsize itself and meet the business where it is.
Simon Moffatt has nearly 25 years experience in IAM, cyber and identity security. He is founder of The Cyber Hut - a specialist research and advisory firm based out of the UK. He is author of CIAM Design Fundamentals and IAM at 2035: A Future Guide to Identity Security. He is a Fellow of the Chartered Institute of Information Security, a regular keynote speaker and a strategic advisor to entities in the public and private sectors.