
SGNL’s integration with Jamf brings real-time device trust into every access decision, ensuring that only secure, compliant endpoints can reach your most critical systems.

In today’s security landscape, the perimeter is no longer a fortified wall; it’s a dynamic, ever-shifting collection of users, devices, and data. Unsecured and non-compliant devices represent one of the most significant threats, providing a gateway for attackers to access your most critical systems. A one-time check at the login is no longer enough.
That’s why we’re thrilled to highlight SGNL’s integration with Jamf. This partnership moves beyond traditional access control by incorporating real-time device posture into a Continuous Identity model. By fusing Jamf’s rich endpoint data with SGNL’s dynamic, context-aware access policies, organizations can ensure that access is not just granted, but continuously and rigorously evaluated based on trust.
“Our integration with Jamf empowers organizations with real-time access control based on device compliance. This is especially valuable for prioritizing critical systems where the threats can be especially damaging.” - Erik Gustavson, Co-Founder & Chief Product Officer, SGNL
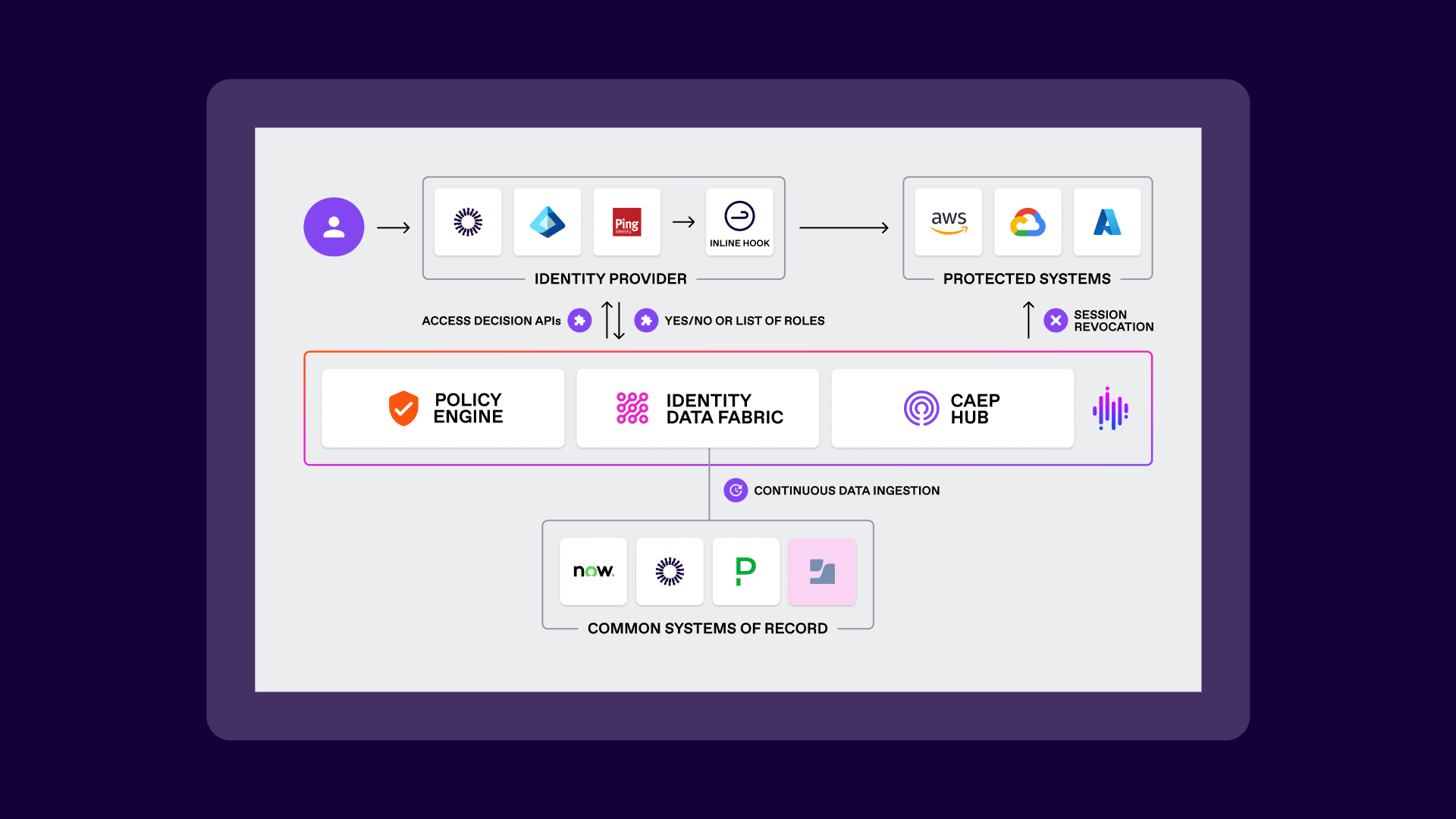
The SGNL and Jamf integration provides a seamless, powerful layer of security that operates continuously without disrupting your existing workflows. Here’s how it creates a more resilient security posture:
Continuous data ingestion: SGNL’s identity data fabric continuously ingests real-time device compliance and security posture data from Jamf.
Contextual policy evaluation: When a user attempts to access a protected system, SGNL’s policy engine evaluates the request against your predefined policies. This decision is enriched not just with identity information, but with live device posture data from Jamf.
Proactive access control: Access is granted only if the device meets the strict compliance standards you’ve set. If a device is non-compliant or unmanaged, access is denied at the door, preventing a potential threat before it materializes.
Responsive access revocation: Trust is not static. If a device’s security posture changes at any time—for instance, if Jamf detects a vulnerability or a user disables a required security setting—SGNL receives this signal and can automatically revoke the active session in real-time. This eliminates the exposure window attackers often exploit.
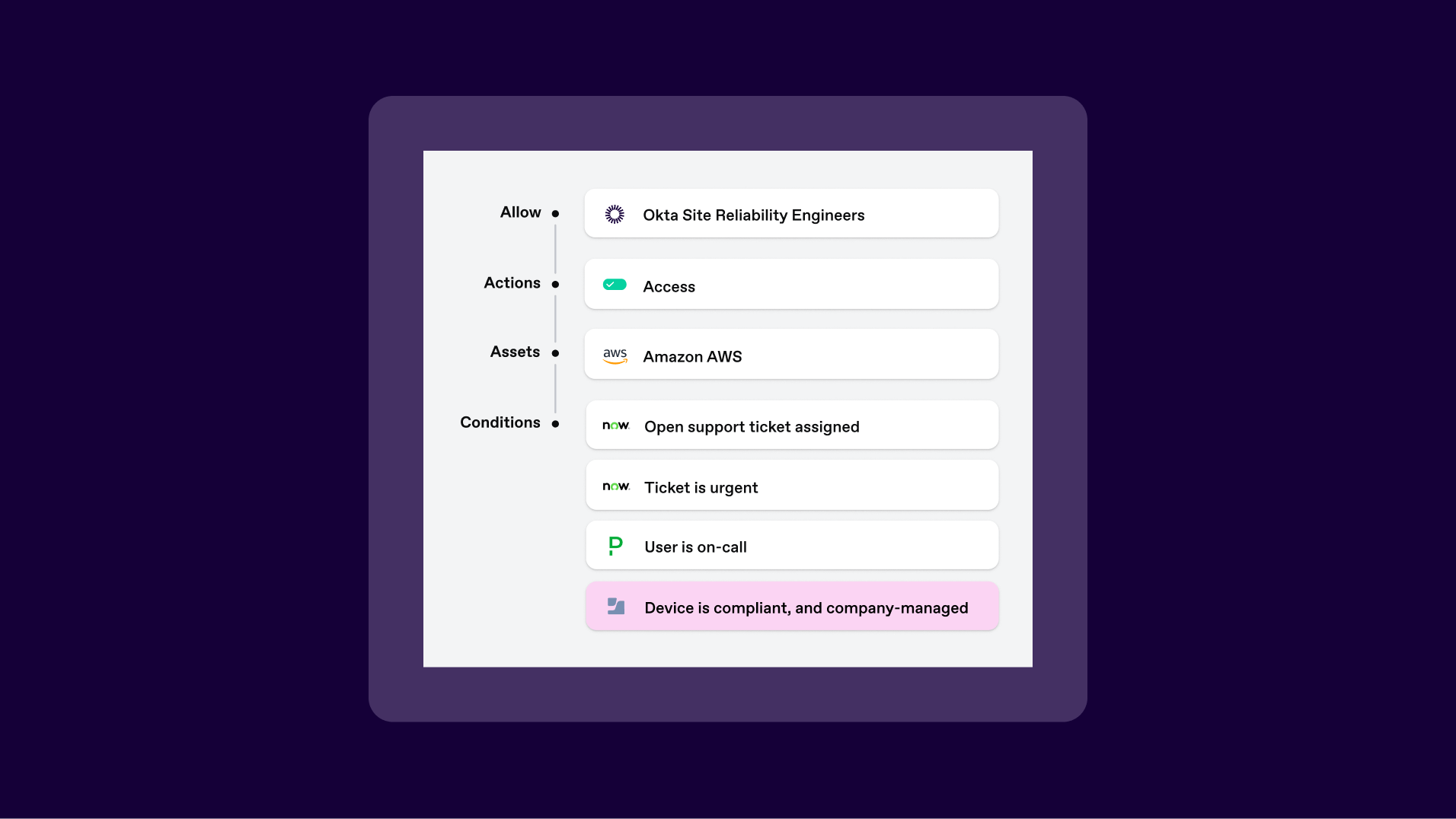
Imagine a site reliability engineer needs emergency access to your production AWS environment. With SGNL and Jamf, access is granted only if all contextual conditions are met:
They are assigned an urgent support ticket in ServiceNow.
They are the designated on-call engineers in PagerDuty.
Crucially, their device is verified by Jamf as company-managed and fully compliant.
The result? The engineer gets the precise, time-bound access they need to resolve the issue, but only from a trusted, secure device. If that device falls out of compliance for any reason mid-session, SGNL immediately terminates the connection, safeguarding your infrastructure.
Integrating SGNL and Jamf delivers powerful benefits that strengthen your entire security program:
Real-time device compliance enforcement: Ensure only secure, managed devices can connect to your most important systems and data.
Dynamic access controls: Leverage Jamf’s device risk data to dynamically adjust permissions, preventing risky devices from accessing sensitive information.
Automated threat response: When Jamf flags a non-compliant device, SGNL automatically revokes access, reinforcing your zero-trust architecture with proactive Identity Threat Detection and Response (ITDR) capabilities.
Strengthened compliance: Consistently enforce device management policies required by frameworks like NIST and CIS.
An open, interoperable ecosystem: Built on the Shared Signals Framework (SSF), this integration ensures seamless communication, giving your security team a unified view of both device and identity risks.
The future of security is built on continuous, context-aware decisions, and the integration between SGNL and Jamf is a perfect example of this principle in action.
We’re excited to announce that we will be demonstrating this powerful integration live at the JAMF Nation User Conference (JNUC) in Denver, Colorado, from October 7-9, 2025.
Stop by SGNL booth #533 or schedule a meeting with the SGNL team to see firsthand how you can leverage Continuous Identity and real-time device trust to protect your most critical assets. We look forward to seeing you there!
Want more of the latest identity-first security topics and trends delivered to your inbox? Helpful and insightful content, no fluff.