
Just-in-time access promises to solve standing privilege problems, but time-boxed credentials with broad entitlements still leave exposure windows that attackers can exploit.

When security teams talk about “reducing standing access,” just-in-time (JIT) access often comes up as the quick fix. Instead of keeping the doors to sensitive systems unlocked indefinitely, you grant access only when someone requests it, for a limited window of time.
On the surface, this feels like a win. Shorter windows, fewer credentials floating around, less opportunity for attackers. But here’s the uncomfortable truth: JIT access without context is still a form of standing access. It just comes with a timer attached.
And as every CISO knows, attackers don’t care about your timer.
If you step back, JIT access looks suspiciously like the very thing it’s supposed to replace.
Think about it: if a user can request two hours of access whenever they want, that’s not really restricted access at all. It’s pre-authorized standing access with a timer. From an attacker’s perspective, it’s the same as a permanent entitlement. Compromise the account and you can spin up access on demand. That doesn’t add protection; it just shifts where the risk shows up.
That’s why calling JIT a “solution” to standing privilege is misleading. It’s more accurate to say JIT reduces duration, but it does not reduce risk.
JIT access policies usually say something like: A developer can elevate their privileges for 2 hours. That’s undeniably better than leaving an admin credential live for months… but think about what happens during those two hours.
All JIT has done is shrink the size of your exposure window, not eliminate it. That’s why breaches keep happening even in organizations that have embraced JIT strategies. A shorter leash is still a leash.
Access decisions don’t exist in a vacuum. The moment you hit “grant,” the world starts to change. Credentials might be compromised, and an attacker doesn’t need the full two hours — five minutes is more than enough to do damage. Business needs may also shift. An urgent database patch might take only 15 minutes, but the elevated session continues running for the remaining 105. Meanwhile, the user’s security posture can degrade in real time: a device falls out of compliance, or a login suddenly comes from an unexpected location, and the system doesn’t notice because the window is already open.
JIT works on the assumption that conditions will stay static between “access granted” and “access expired.” In reality, cloud environments move at machine speed, and that assumption almost never holds up.
On paper, JIT makes audits look neat and tidy. Permanent admin rights don’t show up, so reports appear cleaner. But that neatness is misleading. Every JIT grant still has to be justified and reviewed, because the responsibility doesn’t disappear just because the entitlement isn’t permanent. What’s more, those temporary elevations often slip through standard audit reports. A session that lasts only two hours may never show up in the entitlement list at all, even though the user had full privileges during that time.
The lack of visibility creates another problem: patterns of behavior are almost impossible to spot. Someone who constantly requests elevated access looks no different in a static review than someone who never does. Both appear as if they have no standing privileges, when in reality one of them may be opening the door to risk again and again.
It’s a bit like walking through an empty office on the weekend and concluding that no one works there. The desks may be clear, but the employees still exist. JIT gives auditors that same distorted view — the activity is real, but the vantage point hides it.
The real shift comes when access isn’t tied to a timer at all but to the live conditions surrounding the request. Instead of assuming nothing changes during a two-hour session, the system keeps checking whether access is still justified. That means looking at the business activity — does the user’s task still require elevated rights, or has it already been completed? It means monitoring the device — is it still compliant, patched, and healthy, or has it drifted out of policy mid-session? And it means watching environmental factors — is the login still coming from the expected network location, or has the user’s behavior suddenly deviated from normal?
With real-time context in play, access adapts as conditions evolve. If the signals shift, the privileges shift with them. Instead of granting a block of time and hoping for the best, access is continuously verified against what’s actually happening in the moment.
This is what SGNL calls Continuous Identity: replacing static windows with live decisions.
Here’s how it looks in practice:
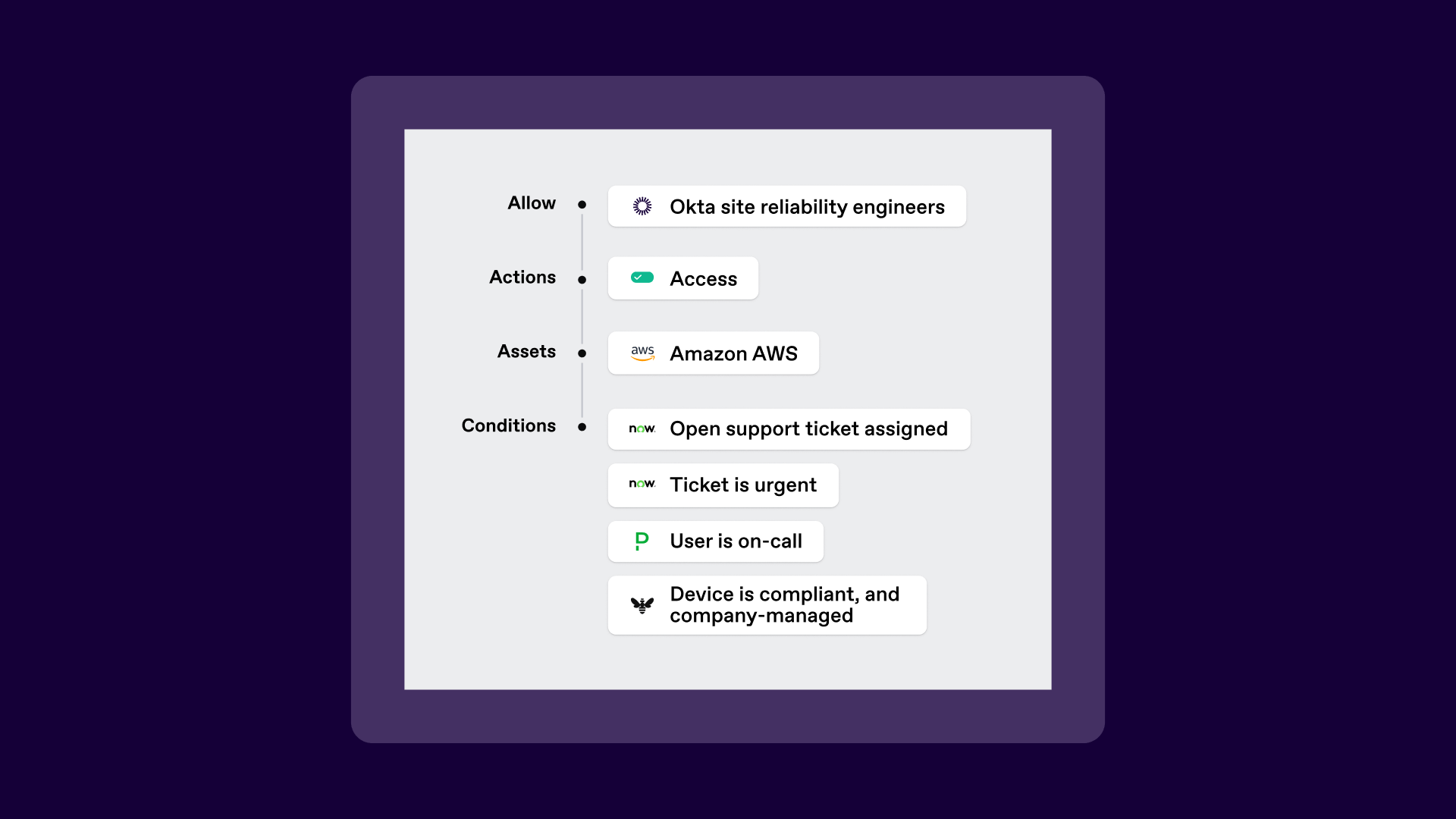
Instead of a two-hour block of standing access, you get access that adapts in real time. The exposure window disappears because there is no window.
Cloud environments move too fast for timer-based security. JIT can make compliance teams feel better, but attackers move faster than compliance checkboxes.
That’s why Continuous Identity isn’t a “nice-to-have.” It’s the only way to align access with the actual pace of your business and the threat actors who target it.
If JIT is the centerpiece of your privileged access strategy, it’s time to take a closer look. Ask yourself:
The good news is you don’t have to rip out your existing IAM stack to get there. SGNL integrates with your IGA, PAM, IdPs, and cloud providers to make them smarter by adding real-time context, orchestration, and continuous evaluation.
Zero Standing Privilege isn’t about shorter windows. It’s about eliminating them altogether.
Want to learn how to close the gaps JIT leaves behind? Book 15 minutes in our Expert Hours. No slides. No sales pitch. Just straight answers.
Want more of the latest identity-first security topics and trends delivered to your inbox? Helpful and insightful content, no fluff.