
The breakdown on how to eliminate standing AWS privileges by connecting your existing tools—Okta, ServiceNow, PagerDuty, and CrowdStrike—into a Continuous Identity architecture that grants just-in-time access based on real-time context.

If you run production workloads in AWS, you already know the pressure: engineers are on call 24/7, incidents escalate in minutes, and attackers only need one credential to walk through the door.
The problem is that most access controls in AWS haven’t kept pace. Standing access is everywhere in the form of persistent IAM roles, long-lived credentials, and blanket privileges that stay open long after they’re needed. Even if you’ve bolted on processes like ticket checks or on-call approvals, they’re often manual and slow. The result? Audit gaps, frustrated engineers, and exposure windows ripe for abuse.
You’ve probably invested in the usual suspects:
But these systems don’t talk to each other. Access is granted upfront, without considering why it’s needed or when it should end. PAM tools may reduce credential sprawl, but they’re still built on static roles and delayed revocation.
That’s where Continuous Identity comes in.
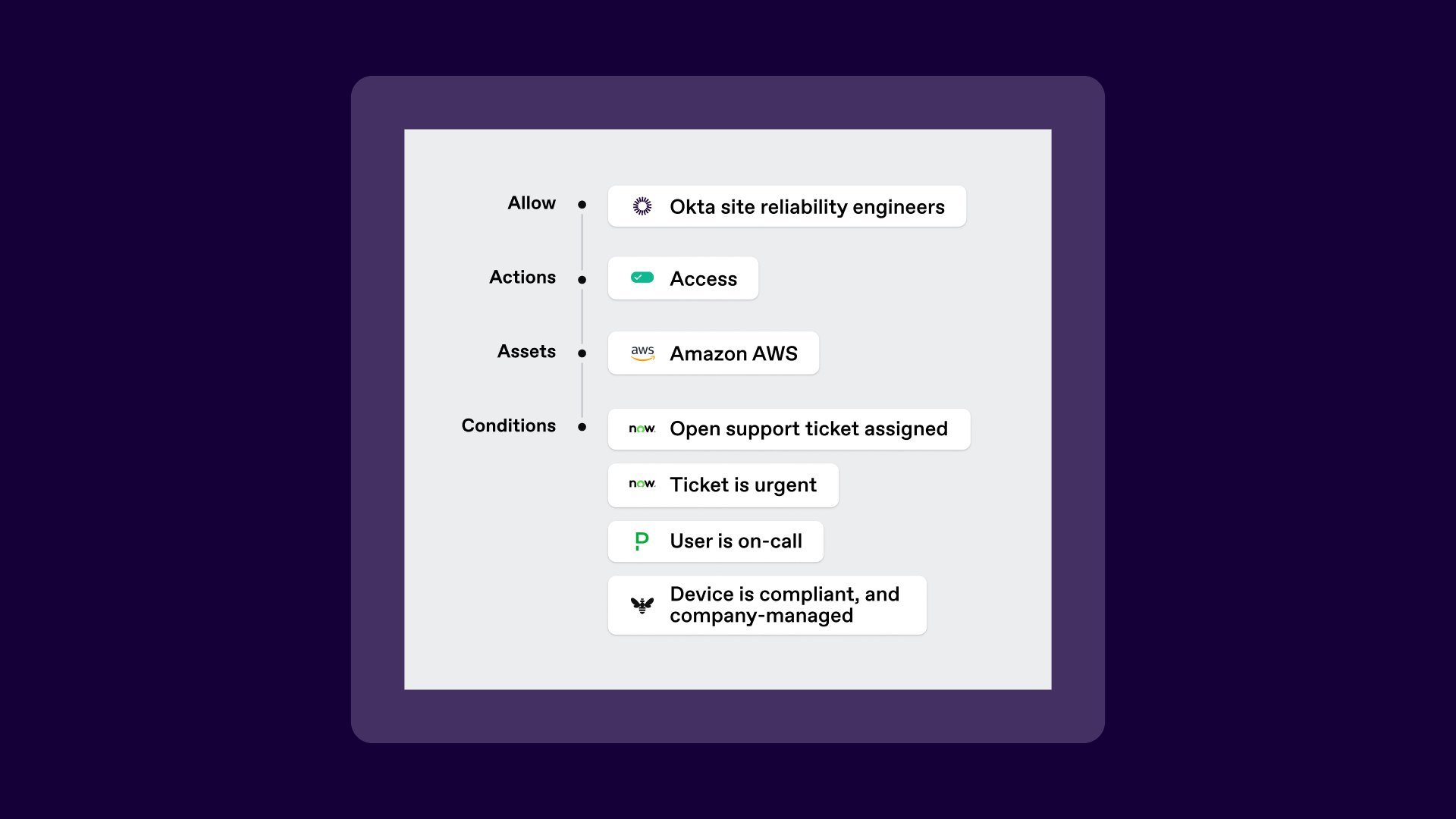
Continuous Identity means making every access decision in real time—based on who the user is, why they need access, when they’re asking, and what device or system they’re using. With SGNL, those checks happen automatically, so engineers get the right access at the right time, and attackers don’t get lingering privileges to exploit.
Here’s how it works in AWS:
No standing roles. No leftover credentials. No exposure window.
And most importantly, no change to how engineers request or access the systems they need.
They still use the same tools—Okta, ServiceNow, PagerDuty, AWS CLI—but behind the scenes, SGNL makes the access smarter, safer, and fully contextual.
Security improves, but the workflow stays familiar.
Organizations deploying SGNL with AWS see:
You don’t need to rip and replace. Most deployments start with:
From there, SGNL connects the dots: our Identity Data Fabric ingests context, the Policy Engine evaluates it, Provider Hooks tie into Okta, and the CAEP Hub manages AWS sessions in real time. Start small. Secure one AWS account, one team, or one critical workflow. Then expand. Each step reduces standing privilege and closes exposure windows—without slowing your people down.
Want the details? Check out the AWS Deployment Guide or learn more about Continuous Identity