
The traditional IAM playbook is failing at machine speed—here’s why Continuous Identity represents the generational shift identity teams need to understand and adopt now.
You know that feeling when you’re explaining to leadership why the identity program you’ve spent years (and maybe millions of dollars) building still can’t prevent the latest threat technique involving compromised credentials? Yeah, that one. The “we did everything right, but…” conversation that makes you question whether we’re fundamentally approaching this wrong?
Spoiler alert: we are.
Here’s the uncomfortable truth our industry needs to face: the traditional IAM playbook (built around joiner/mover/leaver events, periodic access reviews, and human-in-the-loop approvals) is operating at a fundamentally different speed than both modern business and modern threats. We’re playing checkers while the world moved to chess, then to speed chess, and now we’re somewhere in the realm of holochess or tri-dimensional chess depending on your favorite space-based version of the future.
Let’s do some quick math that should make every identity practitioner uncomfortable. During a typical business day, how many actual joiner/mover/leaver events occur in your organization? Maybe dozens? Now compare that to how many access decisions your systems make. Thousands? Tens of thousands? The ratio is absurd. What about login you might ask? Same story… and don’t even ask about logout.
We’ve built an entire discipline around managing identity at the pace of HR processes while access happens at the pace of business. And then we act surprised when attackers exploit the massive gaps in between.
Consider this: your star developer gets their laptop compromised on Tuesday morning. In the traditional IAM world, when do you find out? When do you act? If you’re lucky, your SOC catches suspicious behavior by Thursday. Your incident response team investigates through Friday. By the following Tuesday (a full week later) you might have deprovisioned their high-privilege access. Maybe.
Meanwhile, that compromised identity has had seven days to quietly explore your environment, escalate privileges, and establish persistence. Are we really going to keep calling this “security”?
Here’s another problem we’ve normalized: people accumulate access like they accumulate browser tabs. Sure, they needed that database admin access for the migration project six months ago. And yes, they required those AWS permissions for the cloud initiative last quarter. But those projects are done, the contexts have changed, and the access remains.
We tell ourselves that’s what access certification campaigns are for. But let’s be honest—asking managers to review spreadsheets of access they don’t understand, for systems they’ve never heard of, every six to twelve months isn’t risk management. It’s security theater.
The real kicker? Even when those campaigns work perfectly (and they rarely do), you’re still operating with up to a year of exposure window. That’s not acceptable in an environment where attackers measure their operations in hours and days, not quarters.
This is where Continuous Identity (CI) comes in—not as another vendor-coined buzzword, but as a fundamental rethinking of how identity controls should work in modern environments.
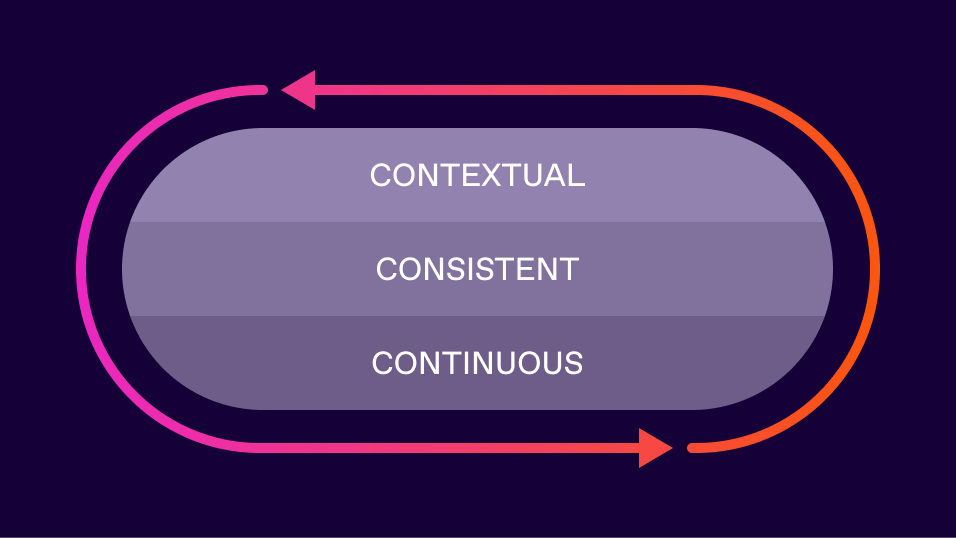
Continuous Identity represents a generational shift from event-driven IAM to context-driven access. Instead of waiting for the next joiner/mover/leaver event or the next login attempt, CI continuously evaluates access based on real-time business, security, and environmental context.
Contextual: Access decisions informed by meaningful, real-time context that traditional IAM systems could never reach. Is the person on duty? Are they working on a managed device? Has their behavioral risk score changed? Is there an open ITSM ticket for the system they’re accessing? This isn’t just fancy attribute-based access control. It’s about making identity controls aware of the business context they’re supposed to protect.
Consistent: The same policies, enforced the same way, whether you’re dealing with SSO flows, access requests, application authorization, or even AI agents trying to access resources. No more policy silos creating gaps attackers can exploit.
Continuous: When context changes (when a device gets compromised, when someone goes off duty, when a security incident is declared) identity controls react immediately. Not at the next login. Not when someone remembers to check. Immediately.
I know what you’re thinking. “This sounds expensive and disruptive.” Here’s the thing: you don’t have to throw out your existing IAM investments. In fact, you shouldn’t.
The beauty of Continuous Identity is that it’s designed to evolve your current infrastructure, not replace it. Those contextual policies can enhance your existing IdP deployment. And then the same consistent enforcement can improve both your IGA approval workflows. And when context changes trigger remediation actions, they can work through your existing tools. They tell your existing IGA to deprovision privileges, instruct your existing identity provider to terminate sessions, and alert your incident response team.
You can start small. Pick a high-value use case:
These aren’t theoretical examples. Forward-thinking organizations are implementing exactly these kinds of controls today. Shameless plug for SGNL’s Expert Hours offering - schedule time and get some insight on how others are handling any specific issue that’s top of mind for you.
The identity industry loves to talk about zero trust, but most implementations stop at “never trust, always verify” except without addressing the “always” part. How do you verify continuously? How do you maintain that verification as context changes throughout a user’s session?
That’s what Continuous Identity solves. It’s not just about better authentication or smarter authorization. It’s about making identity controls that can keep pace with both business velocity and threat actor sophistication.
The organizations that figure this out first will have a significant advantage. They’ll be able to enable business agility without sacrificing security. They’ll reduce their attack surface while improving user experience. They’ll turn their identity program from a cost center that slows things down into a competitive advantage that enables speed.
The rest will keep having those uncomfortable conversations with leadership about why their identity investments didn’t prevent the latest breach.
At SGNL, we’ve been thinking about this problem from the ground up. We built the first platform specifically designed to deliver Continuous Identity by centralizing all that fragmented context into real-time decision intelligence that can evaluate and orchestrate access at the speed of business. But honestly, the vendor doesn’t matter as much as the concept. What matters is that you understand this shift is happening, with or without you.
The question isn’t whether Continuous Identity will become the standard. It’s whether your organization will be leading that transformation or playing catch-up.
What’s your take? Are you seeing the pace problem in your environment? Let us know —I’d love to hear how others are thinking about this challenge.