
This promising standard needs security guardrails for enterprise implementations
The Model Context Protocol (MCP) has taken the AI world by storm. The security community has been abuzz with understanding its risks and thinking about potential solutions. This was amply evident in the multiple meetings I had with identity and security practitioners and decision makers, where AI and MCP was a top concern. Recent additions to MCP standardize some aspects of authorization, but the security concerns MCP creates go well beyond what is addressed currently within the protocol.
Although MCP is not widely deployed today in enterprises, its benefits are enormous, and there is a groundswell of demand at many large organizations. So it is prudent to define a security architecture and be prepared to address the need before the data floodgates open.
Large language models (LLMs), are a popular machine learning technology, and pre-trained LLMs generate text or other multimedia output (called Generative Pretrained Transformers - or GPTs). An example of a GPT would be the older ChatGPT model 3.0. Reasoning models - the latest additions in this stack such as Claude 3.7 Sonnet - are trained to break down problems into multiple steps, apply specialized reasoning based on different domains, perform web searches or invoke independent services as required.
This ability of agents to communicate with independent services as a part of the reasoning to solve the current task is where MCP comes in. The user uses an MCP Host on their end, which can use multiple MCP clients, each to communicate with a different MCP server. MCP clients can reside on end-user devices (which is a popular model today) or in the cloud. Clients can make requests to the MCP servers, and MCP servers can notify clients when they have updated results.
The most important component of an MCP server is the tools it provides. A “list tools” method enables an MCP client to discover the tools available in an MCP server. The tools themselves are also invoked like API methods by the MCP client. MCP servers can also support resources and prompts, but those are less commonly used. The diagram below shows the flow diagrammatically:
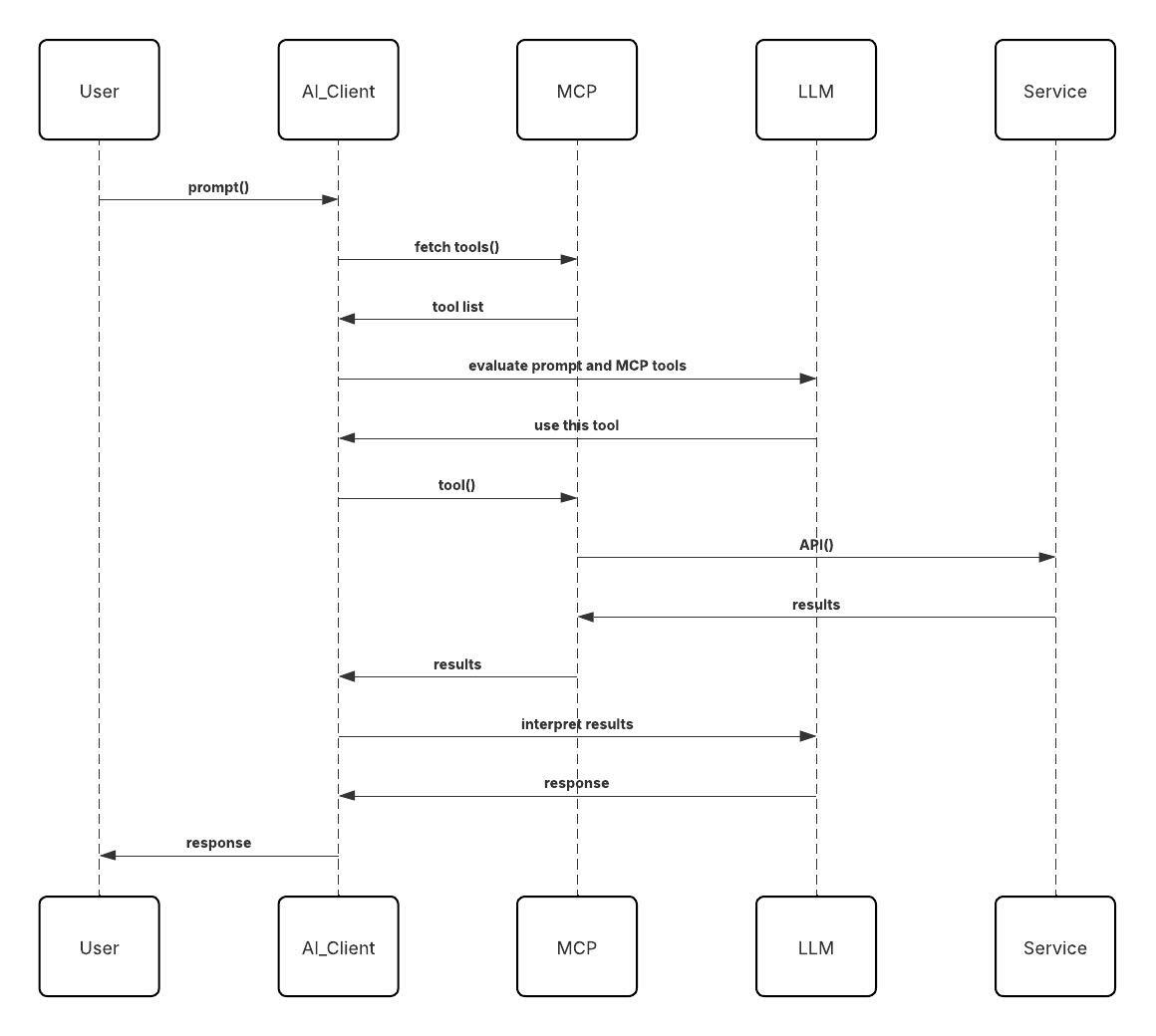
In the above diagram the “Service” is the actual component hosted by the service provider that does the work of completing the user’s request. The MCP box is the MCP Server, which acts as a front-end to the service.
The recent updates to MCP specification (informally called “3-26” for the date when it was updated) adds an Authorization section. While authorization is optional, when it is used, it provides best practices around the use of OAuth 2.1 draft specification (and related standards). Using this capability:
An MCP client discovers required “scopes” and location of the authorization server from the MCP server, and requests authorization from the Authorization Server (AS). The AS is typically your identity provider (IdP).
The AS provides a familiar interface to users that requests their consent to use specific scopes that the MCP Server accepts. The AS should translate the scope into terms you can understand (like when a social media app asks you whether an event booking site can use your profile photo). The example below shows a typical OAuth consent screen (not specific to MCP).
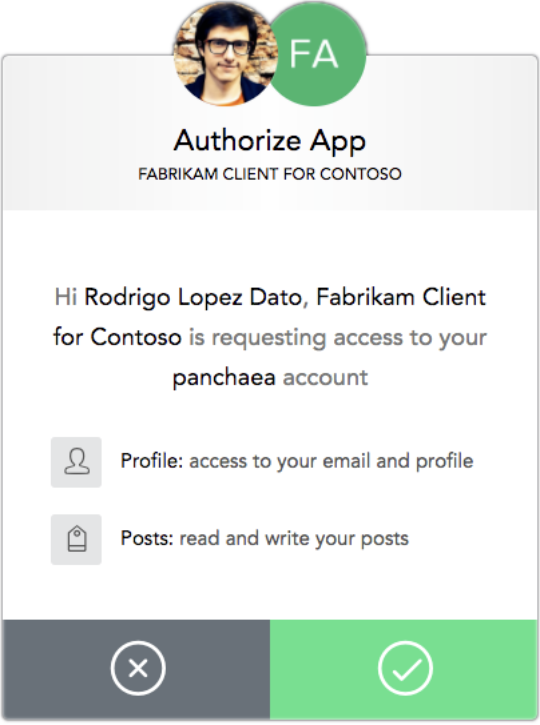
The AS conveys the authorization token (which can include your user identity) to the MCP server
As a result of this, the MCP server knows that the user is OK to use the specific feature of the MCP server for this purpose.
As you can see above, MCP provides a baseline for security. In an enterprise scenario, the AS can determine whether or not the user is permitted to have a token with the requested scope and deny it if the user does not have access to that functionality. However, there are many limitations:
SGNL recently announced an MCP gateway that addresses these security concerns. All you need to do is insert the SGNL MCP gateway between your MCP server and clients that use it. Read the SGNL press release here: With MCP, AI agents now have power. SGNL makes sure they use it responsibly.