
Malicious actors rely on standing access to breach your systems, disrupt business operations, and exfiltrate data.

Nearly 80% of high-profile system outages stem from identity breaches attributable to excessive standing privilege — and the rate of successful attacks keeps climbing up.
All it takes is one targeted identity compromise to inflict a devastating attack. Even as security teams and IT make substantial investments to stop threat actors from infiltrating systems, 79% of CISOs reported SaaS security incidents in their company.
To prevent excessive damage during and after an identity breach, enterprises must focus on reducing their potential “blast radius.”
A blast radius refers to the impact an organization could suffer from a security breach, such as an identity compromise. It represents the scope of damage an attacker can inflict on your company once they’ve gained unauthorized access to your systems.
The term originates from the blast radius of a bomb, describing the physical area affected by the explosion. Similarly, in a cybersecurity context, the blast radius includes the systems that a malicious actor can gain unauthorized access to if they’ve successfully compromised the identity of an employee, contractor, partner, or vendor.
The attacker inherits all the roles and entitlements associated with the compromised identity, meaning a single compromised account can lead to widespread damage if it’s connected to multiple systems and some amount of privileged access.
Unfortunately, the blast radius naturally expands as companies evolve. This is due to:
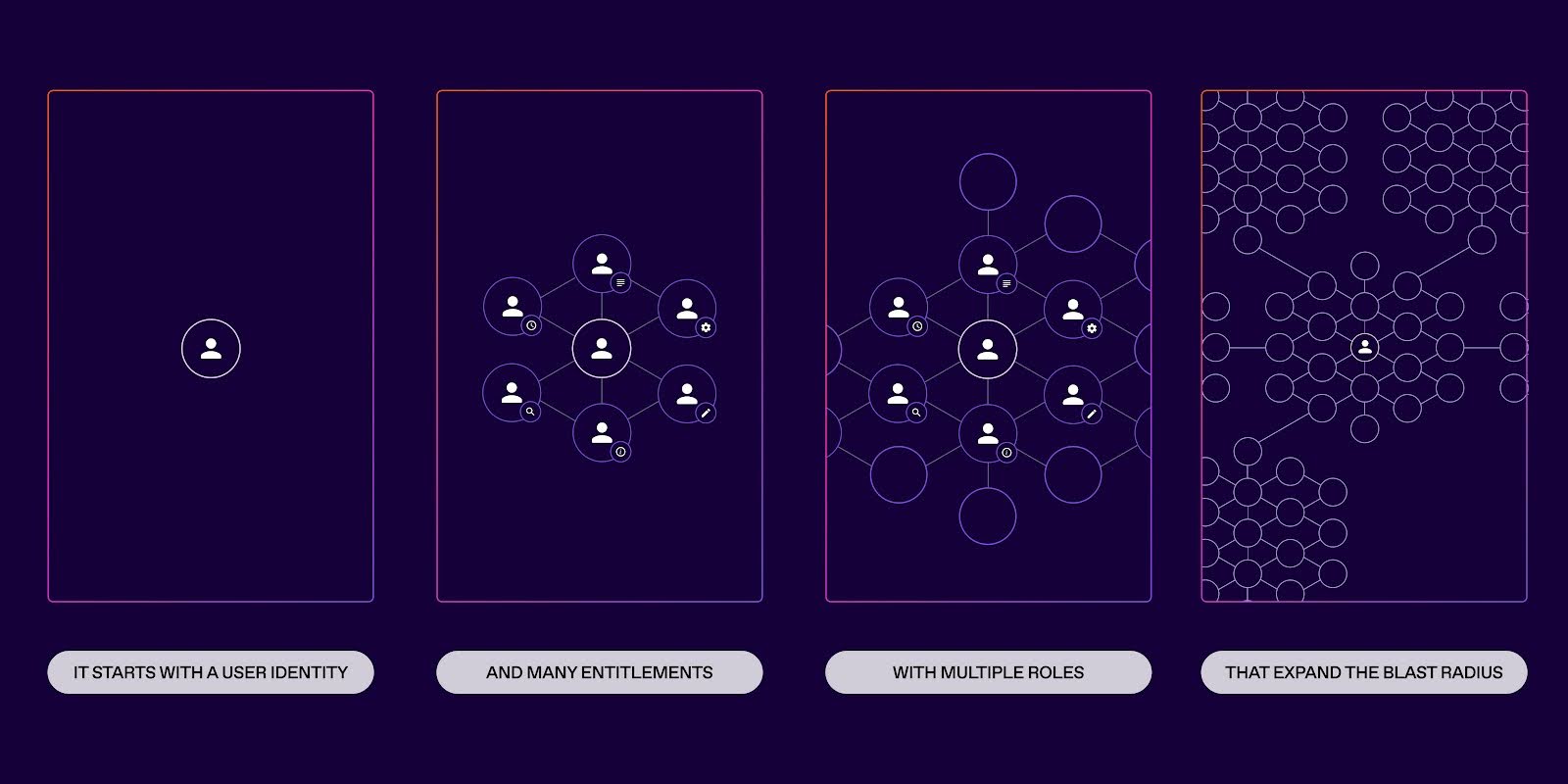
Figure 01. As roles and entitlements are added to cloud and on-prem systems, the potential blast radius increases substantially for all users in the company.
Consider an enterprise company where an employee has access to several critical systems, such as GitHub and AWS. This employee’s identity includes multiple roles (and their subsequent entitlements) that have been granted standing access to these systems.
Because of these privileges, a threat actor can run the following play:
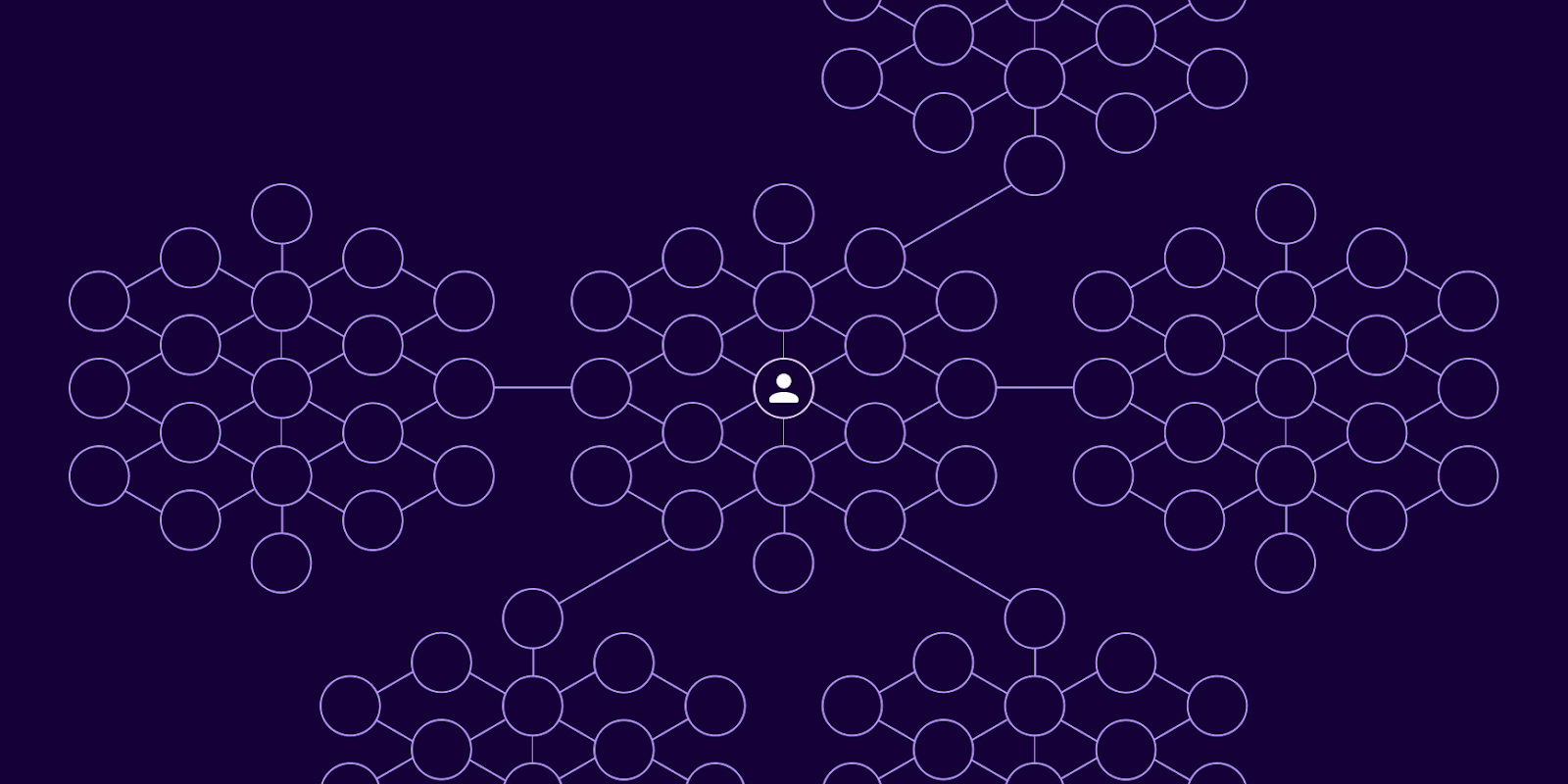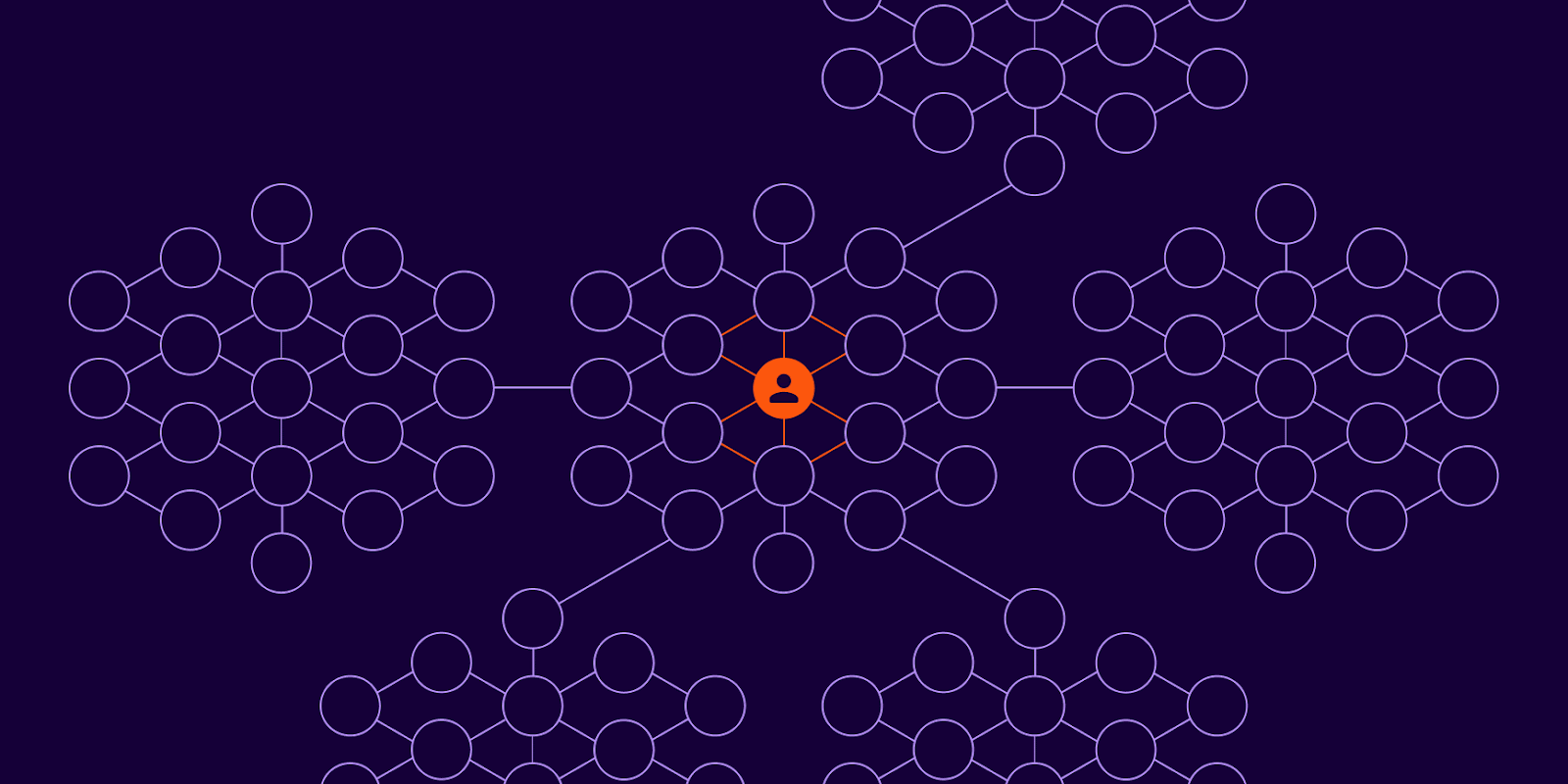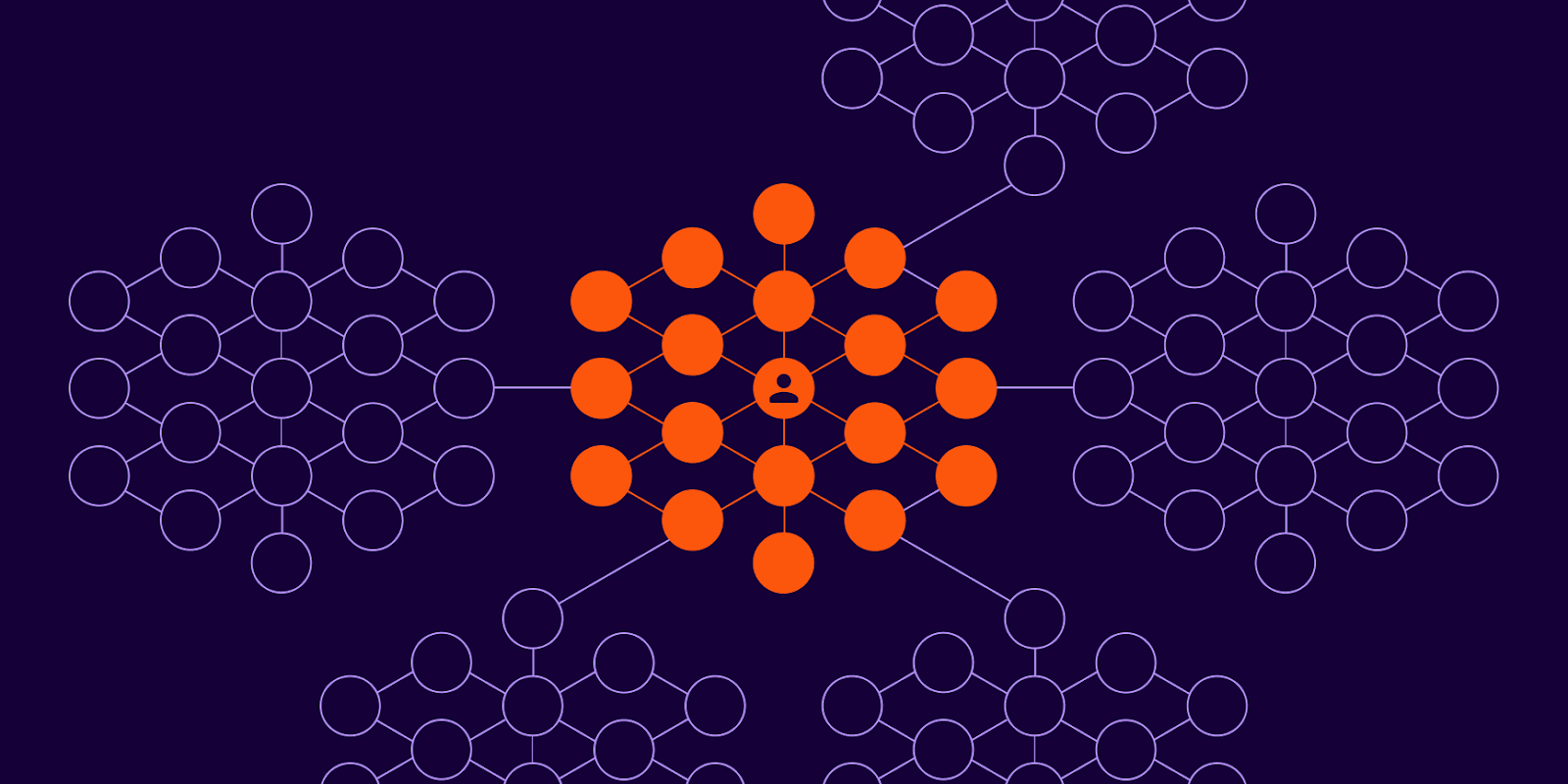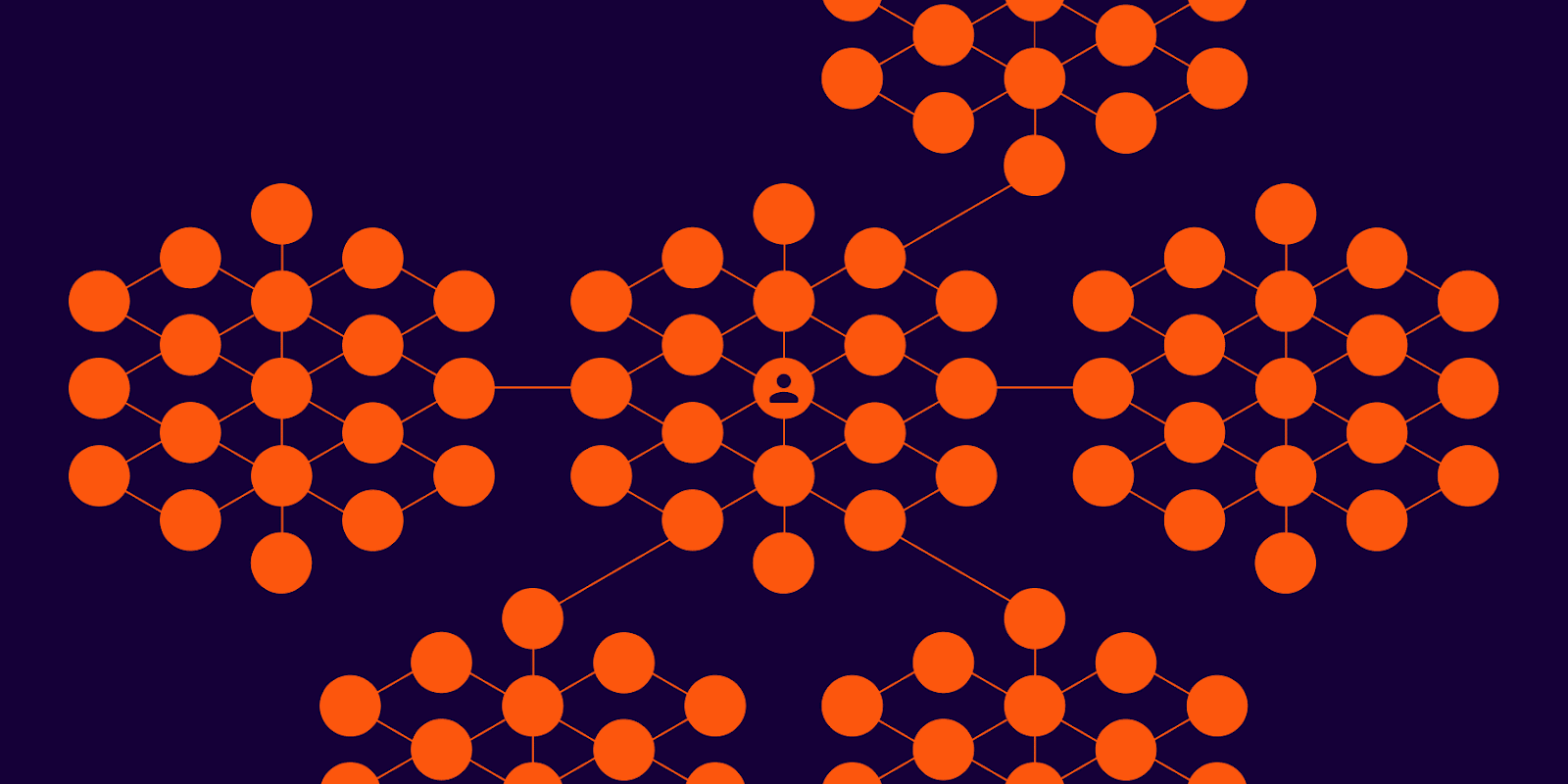
Figure 02. Standing access and excessive privilege allows a threat actor to move laterally across a compromised user identity’s roles and entitlements.
The danger corresponds to the complexity of a user’s entitlements. If the employee can modify user permissions or access administrative functions, the attacker can escalate their privileges, gaining even more control over the network.
Traditional authorization frameworks like identity governance & administration (IGA) and privileged access management (PAM) can make modest blast radius reductions, but these technologies face severe limitations.
IGA is typically employed for birthright access, which are the access rights and permissions automatically granted to employees when they’re hired or change roles. This does help to establish a baseline of limited privileges. But access and entitlements, as illustrated above, change constantly. IGA cannot accommodate the business context for these change requests. As such, the blast radius continually expands.
PAM platforms, as the name implies, secure and manage highly privileged accounts. Most PAM platforms rely on creating and maintaining shared secrets, which are then used to access the critical systems they protect. This added layer of security, in practice, negates the strong authentication features (e.g., MFA or passkeys) those systems, especially cloud-based systems, have in place. PAMs are typically cumbersome and slow to deploy, requiring extensive administrative overhead to maintain access rules. Inefficiencies and delays are common. These high costs stop most PAM customers from making a notable difference in their potential blast radius.
A new authorization framework we refer to as modern privileged identity management (PIM) can drastically cut your blast radius. This access management approach severely limits the impact of an identity breach in two key ways:
SGNL’s modern solution for privileged identity management allows and revokes access in real-time based on changes in context. This dynamic authorization completely eliminates the need for standing access to critical systems. As a result, companies can achieve Zero Standing Privilege (ZSP) and significantly reduce their blast radius.
With SGNL in place, the large blast radius example we shared earlier plays out quite differently:
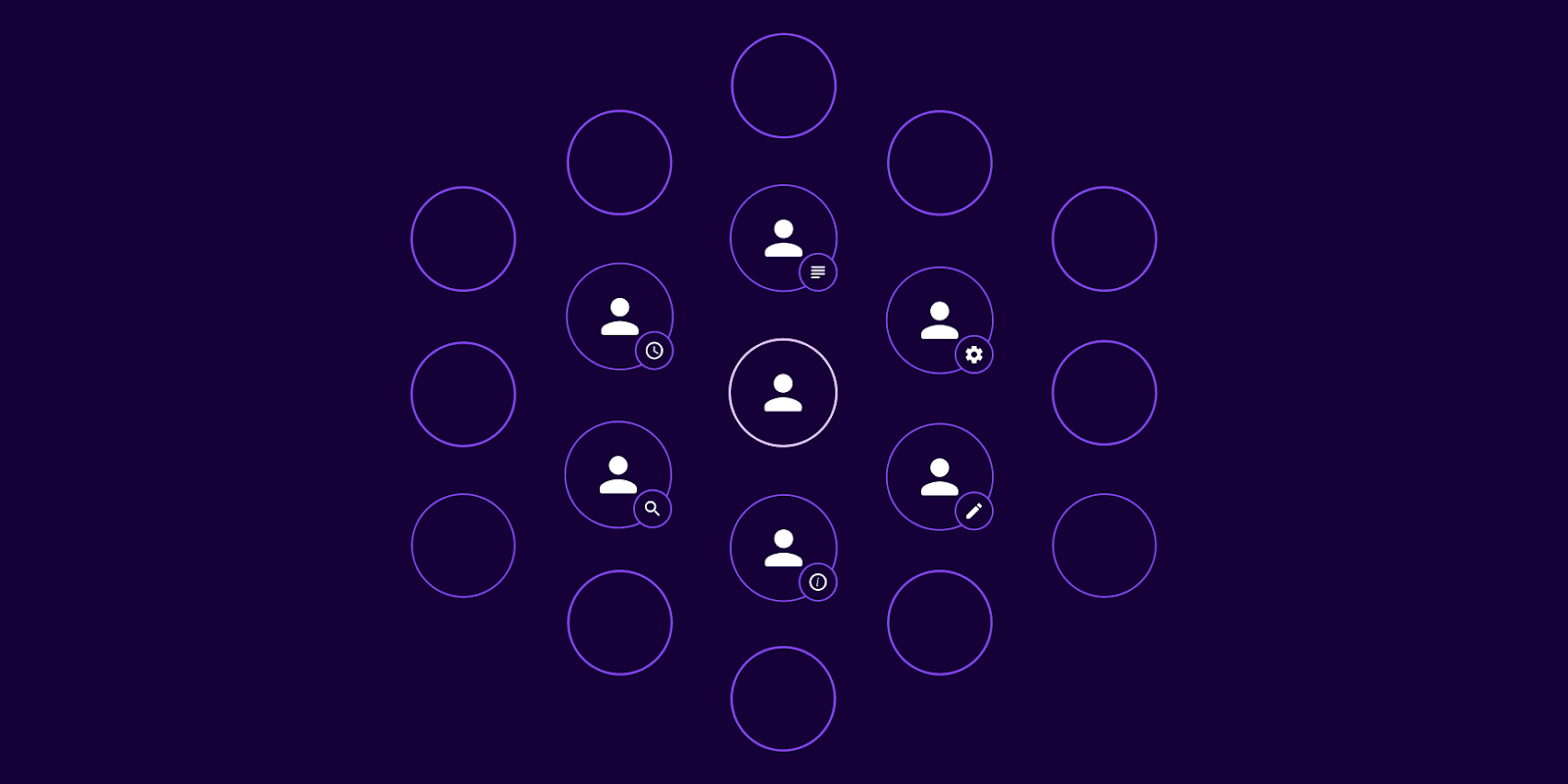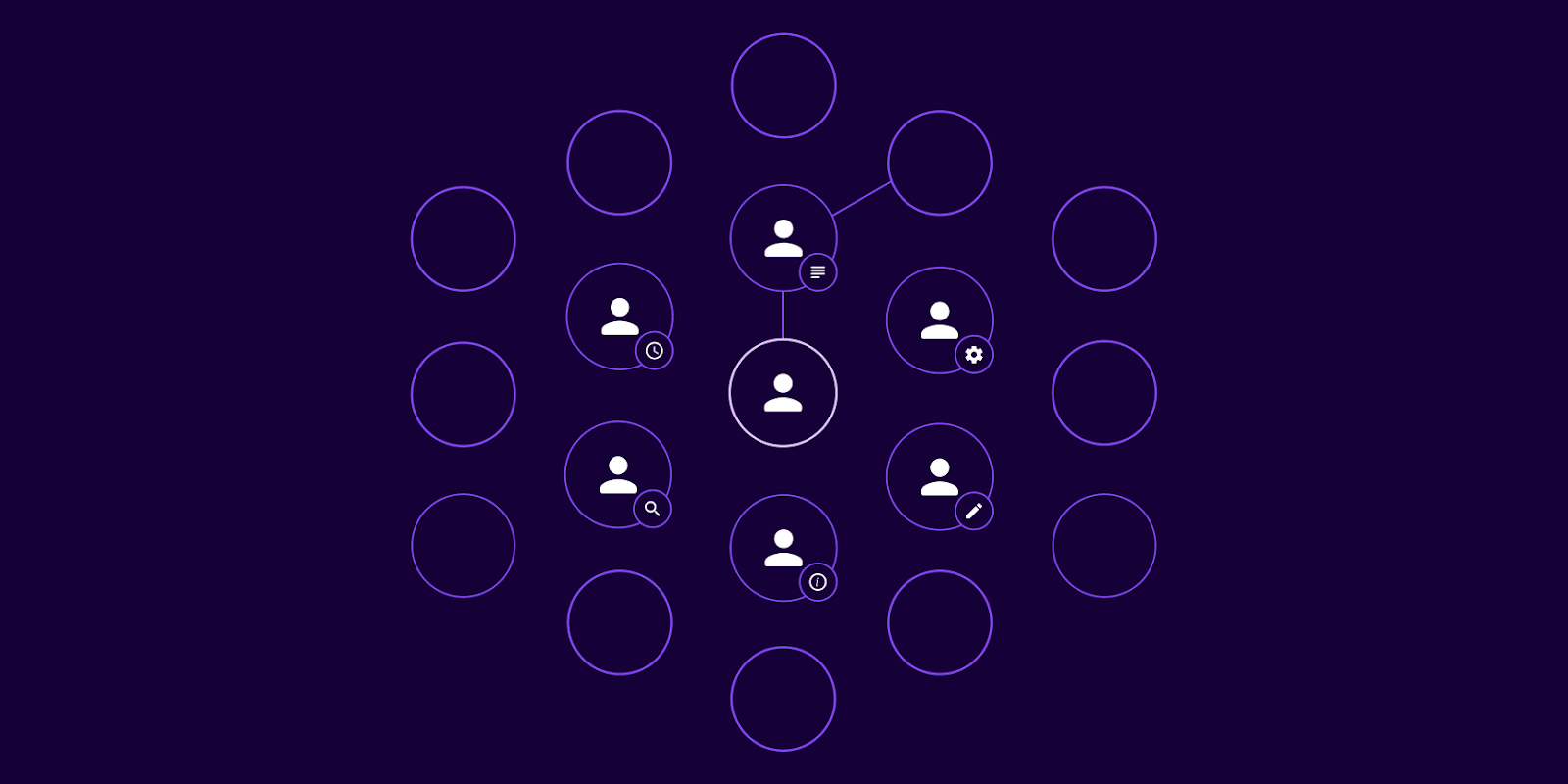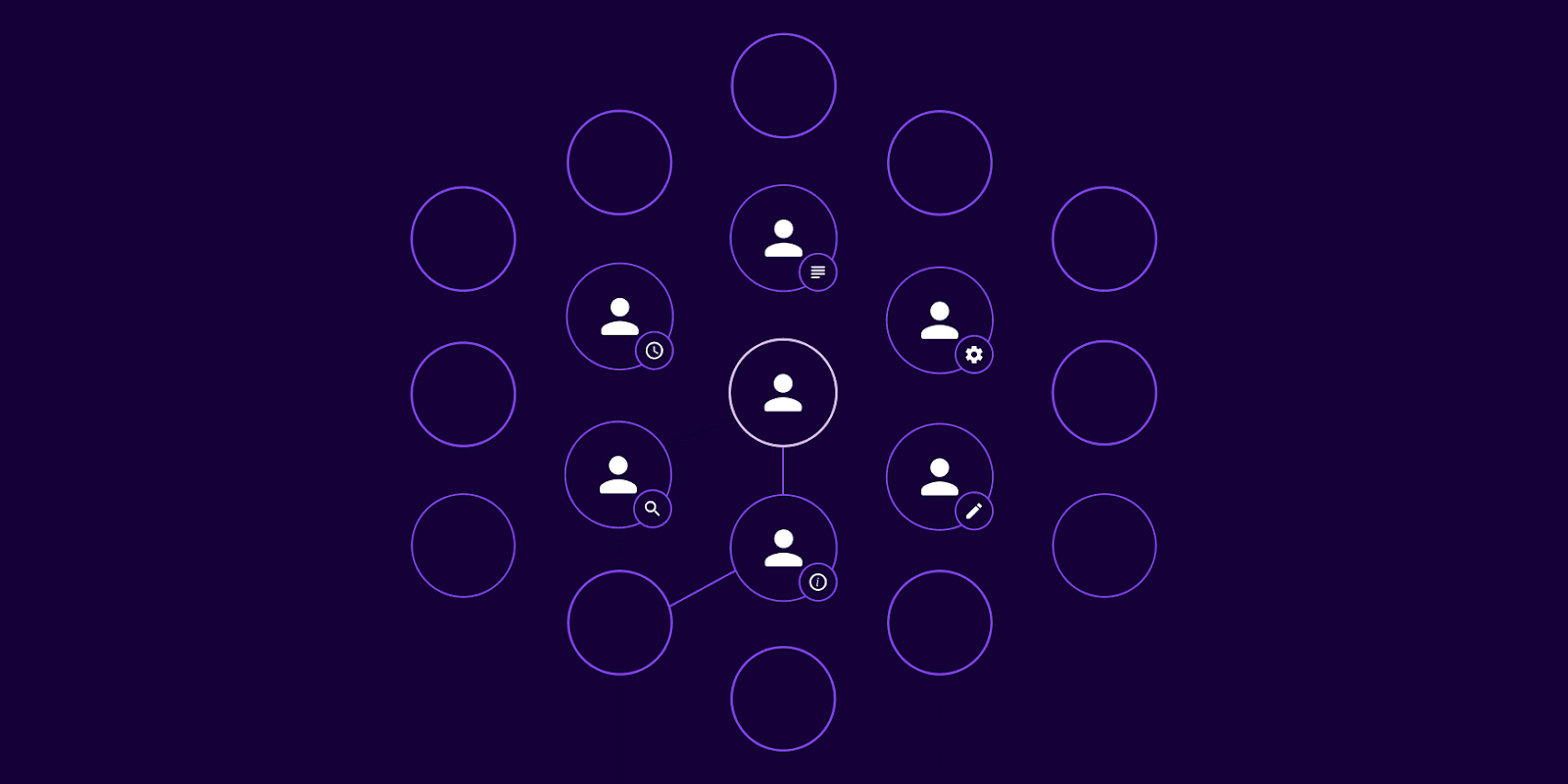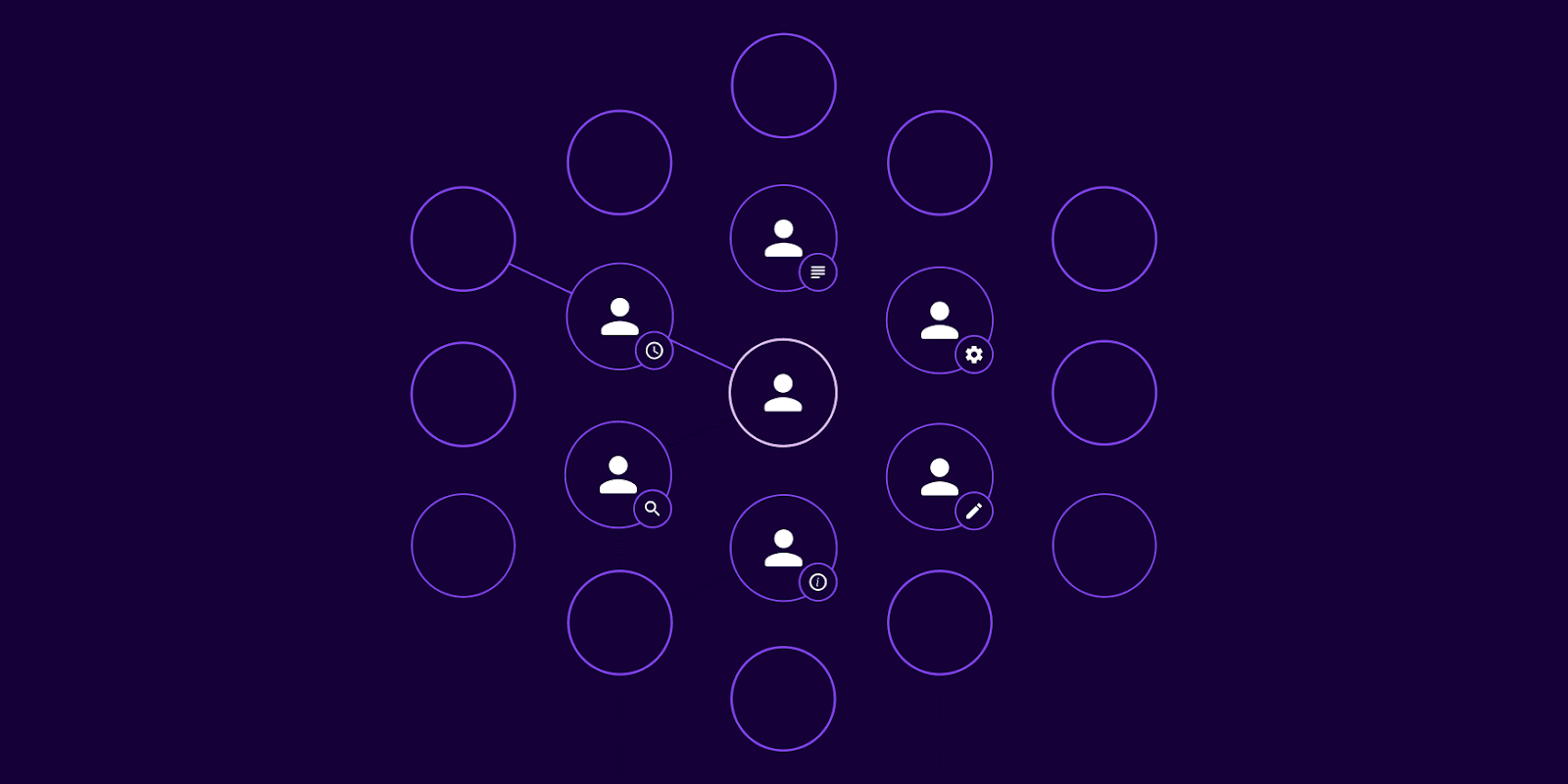
Figure 03. SGNL’s privileged identity management (PIM) solution dynamically grants access for limited timeframes based on established policies and contextual data from multiple systems.
Moreover, SGNL’s solution integrates with the most commonly used IT infrastructure and systems along with custom-built applications, enabling dynamic access management across diverse, often unconnected, environments. This further diminishes the potential blast radius by applying access policies consistently and monitoring them continuously.
Adopting modern privileged identity management solutions provides the agility enterprises need to drastically limit the blast radius. See how SGNL can help.