
Examining ACLs, RBAC, ABAC, and centralized authorization for common access control and identity security use cases
As IT organizations struggle to maintain a large number of roles and groups, they typically manage access manually with access control lists (ACLs) or role-based access control (RBAC). Beyond simplifying identity management, access control tools are also critical for limiting users’ access permissions.
After all, rigorous access control is often the only measure that can prevent a compromised user from becoming a serious threat to the company’s highly sensitive data.
As part of our new Preventing Catastrophe When Hackers Compromise Identity white paper, SGNL CTO Atul Tulshibagwale examined today’s most popular access control methods. His summary shows how these access control methods work in practice across most enterprises.
| Access Control Method | Advantages | Limitations |
|---|---|---|
| Access Control Lists (ACLs): A static permissions list set at the application level and maintained by an administrator. | The simplest solution for managing the most privileged administrator accounts that rarely change. | Grants excessive standing access with zero granularity. ACLs cannot scale to multiple applications or handle the complexity of most mature companies |
| Role-Based Access Control (RBAC): A process to grant or revoke individual access permissions to users based on their role (e.g., “Hong Kong Customer Service Rep” or “Corporate Marketing Manager”). | More granularity is available compared to ACLs. Permissions can be set within internal or external systems, such as an application’s native Identity and Access Management (IAM) capabilities. | Even if RBAC software claims to automate the setting of permissions, the processes remain mostly manual. Managers usually rubber-stamp reviews of user roles and permissions, creating excessive standing access. |
| Attribute-Based Access Control (ABAC): A strategy that evaluates attributes of principals (and, optionally, resources) to determine access. For example, ABAC could determine if certain fields in an application are visible to certain users. | ABAC is more dynamic than ACLs or RBAC. Attribute values can be computed based on fast-changing data. As a result, ABAC can be more precise than RBAC. | As an organization’s access policies evolve, code changes are required for all applications using ABAC. The company must manage the universe of attributes precisely. Due to these issues, ABAC adoption is limited. |
| Centralized Authorization: A method of providing just-in-time access decisions from a centralized service, which acts as the Policy Decision Point (PDP). Each application or service relies on this central PDP for decisions at the time of access. | A centralized system accommodates workflows that provide centralized administration and governance. The “fine-grained” access permissions and dynamic access controls scale with the enterprise, enabling minimal administrative burden. | This method sometimes requires changes to applications or services using ABAC. By relying on one central point for access decisions across applications, slow response times or downtimes can disrupt critical operations and limit business efficiency. |
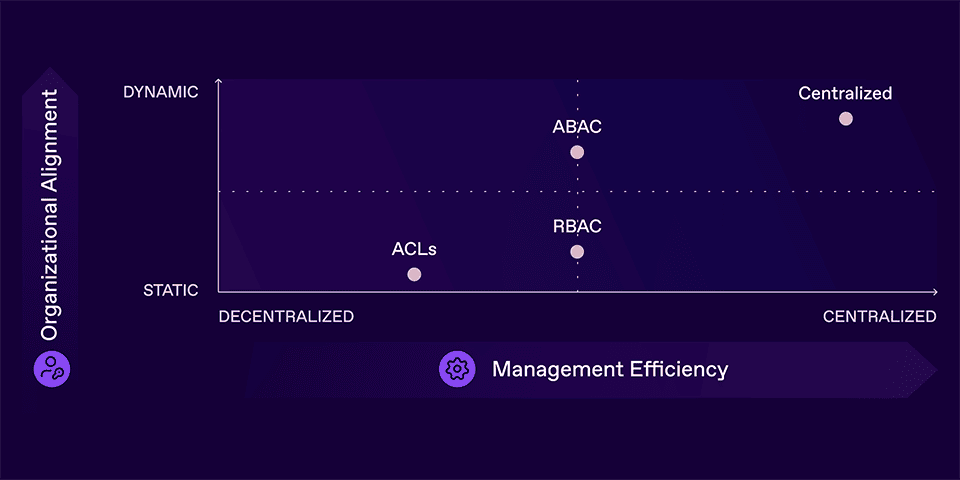
If placed in a chart, access security can be measured by two axes:
Organizational Alignment. This axis shows how well the access permissions reflect what users can access at any given point in time.
For example, does a customer service representative need access to all customers, or just the one whose issue they are currently working to resolve? As you can imagine, static access control models such as RBAC fare poorly in this regard, but dynamic, fine-grained access control solutions rank better.
Management Efficiency. This axis indicates how much effort is required to update any access permission or policy.
For example, how much work is involved to modify an individual user’s permissions across multiple resources? And how much effort is needed to update a policy that dictates how certain resources may be accessed? If you use a centralized identity governance and administration (IGA) tool, updating a user’s permissions may be easy. However, if you want to change what data users with the role “Hong Kong Customer Service Rep” can access, you may need to modify code that explicitly recognizes those users within each application. Ideally, an organization should be able to make all management actions centrally. Various technologies offer different levels of centralization in this respect.
Based on the above criteria, typical implementations fall on the landscape accordingly:
 Figure 01. Popular access security methods ranked by key evaluation metrics.
Figure 01. Popular access security methods ranked by key evaluation metrics.
As this chart clearly illustrates, centralized authorization provides the best outcome by managing user permissions and policies centrally.
So, why is centralized authorization not being rapidly adopted by all enterprises?
For an in-depth look at overcoming the obstacles of centralized authorization, download our latest white paper.