
In the second part of our series, we leverage continuous access management for a fictitious healthcare API alongside Curity and Kong

In our previous blog we discussed securing APIs and ensuring you are protected for both authentication and authorization while keeping the request context intact. This sounds easy, but to successfully protect your APIs, the system must perform a series of checks, especially the introspection of an access token to retrieve the user’s identity needing authorization. In this post, we will demonstrate the technical solution involving SGNL, Curity, and the Kong API Gateway.
This demonstration showcases access requests to a patient record. In healthcare organizations, it is common for patients to have access to their own patient records, but access should be restricted to view a different individual’s patient records. For example, if Alice attempts to access Bob’s patient data, she should be denied.
This demo implementation includes a sample patient records API which is protected by the Curity Identity Server, SGNL, and Kong. Curity authenticates the user and generates appropriate access tokens. The Kong gateway’s plugins intercept the request for the record data and orchestrates the validation of the identity in the request and enforces fine grained access through the SGNL Kong plugin.
The security solution for the sample patient record data is comprised of three main components:
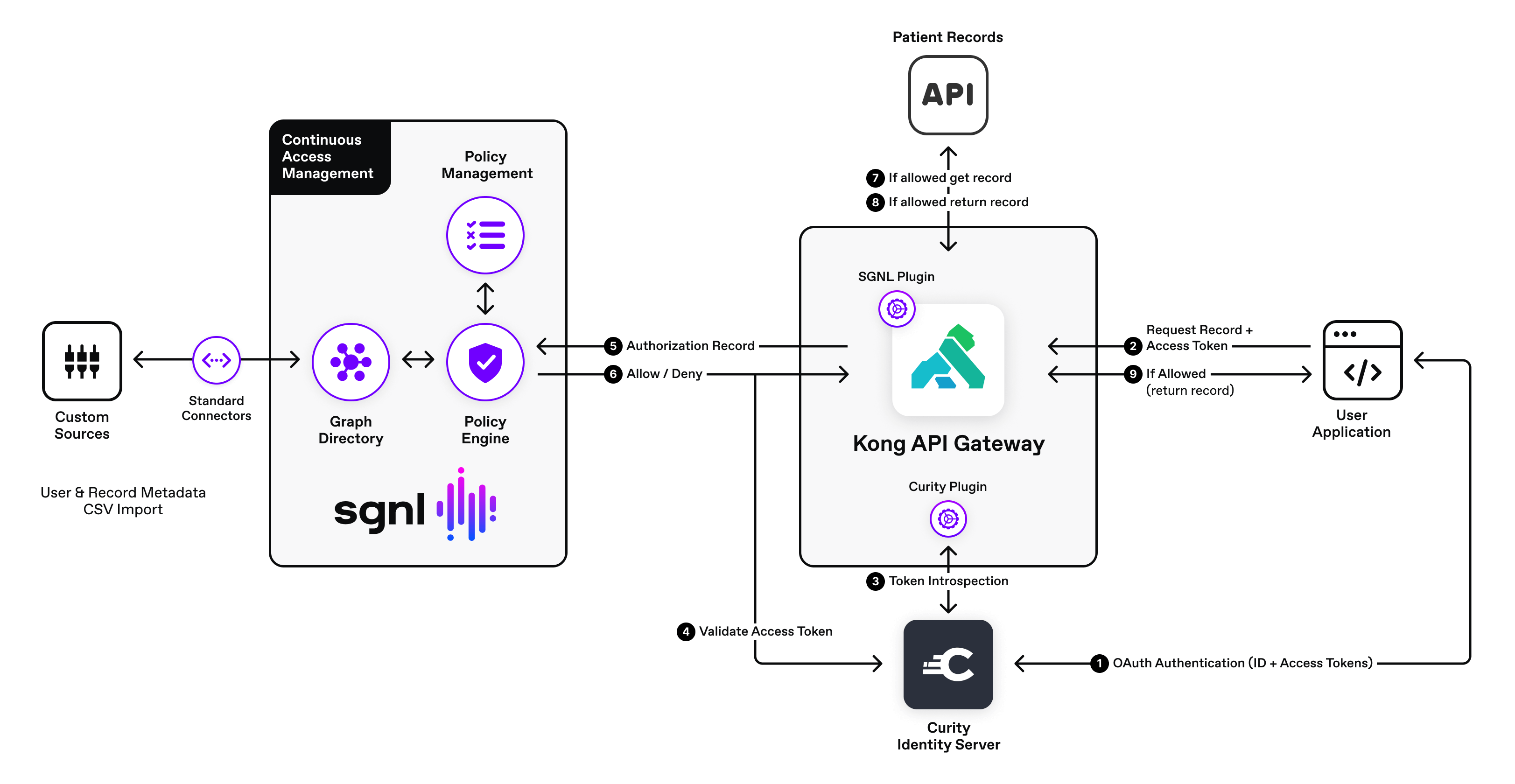
The following is the request sequence initiated by a user application.
Every request for patient records is evaluated against a SGNL human readable policy. The policy below checks the incoming user’s access to their own patient records. The “Patient” snippet checks to see if it’s a valid user making the request. The “GET” represents the HTTP verb sent by the SGNL Kong plugin. The “Record” represents the protected patient record asset. This policy also includes a condition to check if the user is the owner of the record asset being requested.
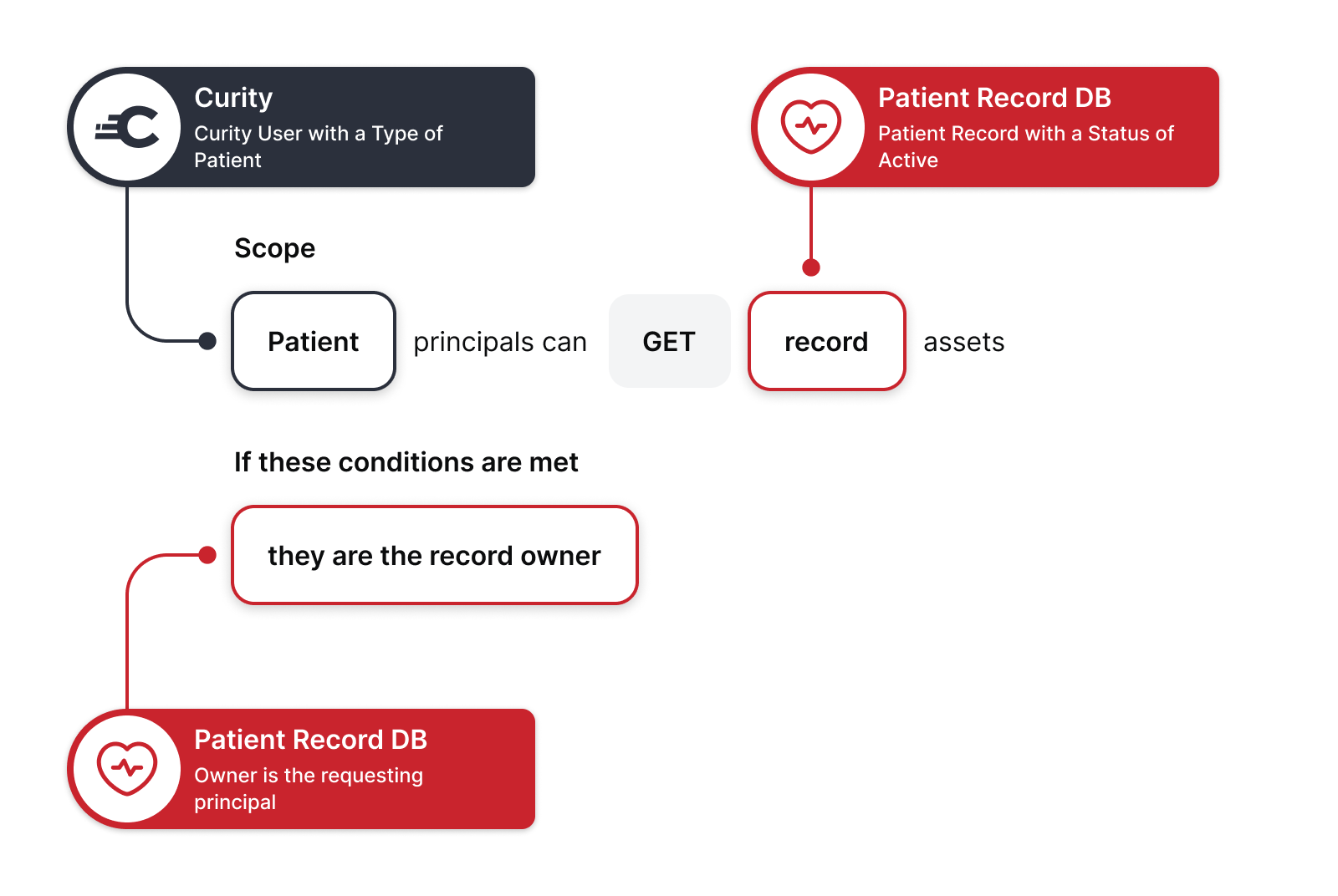
You may download the solution by cloning the examples repository. The solution files are under the curity-sgnl-kong directory. You may find environment setup instructions in the README.md file.
SGNL and Curity enable API defense in depth for APIs. Using SGNL for managing access to your Curity and Kong API Gateway protected APIs, especially high-risk APIs - organizations can reduce risk, minimize authorization logic complexity, and teams can centralize access management policy in a single platform.