
SGNL announced as authorization partner for new Okta product Identity Threat Protection with Okta AI

Today’s opening keynote at Oktane23 ended with the announcement of a new Okta product - Identity Threat Protection with Okta AI (Identity Threat Protection). SGNL is proud to have been named alongside other selected security leaders as a key partner of this new product. SGNL is the only continuous access management platform selected as an Okta partner for this new offering, emphasizing SGNL’s leadership and innovation in identity and access management solutions.
Continue reading to learn more about how identity teams benefit from this partnership, and how implementing SGNL policy management creates a preventative and centralized access management program that enhances Okta implementations for reduced risk.
At Oktane? Meet with SGNL CTO Atul Tulshibagwale to see the demo at Oktane.
For decades, enterprises have relied on static permissions to grant users the superset of application and system access. The result is that users have been granted long-standing, over-permissioned roles and entitlements. This access bloat makes an individual’s credentials an ideal target for modern cyberattacks.
When the employed access control methods are limited to session-initiated authentication, it creates a ripe opportunity for attackers to use compromised identities as a force multiplier, resulting in a massive blast radius during a breach. Unfortunately reports like the 2023 Verizon Data Breach Investigation Report (DBIR) show that more than half of security breaches are caused by a single user’s credentials being compromised. Reports also show that wIth a single credential, hackers can traverse systems and applications across an organization’s digital landscape and cause losses averaging millions of dollars.
In 2019, the inability to dynamically communicate authorization and other session security updates led SGNL’s CTO Atul Tulshibagwale to formalize the Continuous Access Evaluation Protocol (CAEP) – a standards-based foundation for granting privilege when it was needed, and for the communication of relevant access and session events across the thousands of apps within an enterprise, and across multiple organizations.
Authentication platforms like Okta, paired with a continuous access enforcement platform like SGNL, greatly reduces the blast radius of a credential compromise by granting record-level access based on run-time, policy-based access decisions, continuously informed by business context.
Today’s announcement is about improved communication between authentication and identity platforms, and sets the stage for a new way of thinking about access management. When implementing Okta with SGNL, identity teams have the opportunity to listen across their identity ecosystem and leverage broadly-adopted, standards-based frameworks to convey updates to user sessions, state, and access.
With this new approach, we leave a world where permissions accumulate over time and sessions are fixed at an arbitrary time limit, and move to thinking about access as evaluated continuously. With continuous access management, business context informs whether access is granted, the approach is truly a zero trust model and user sessions are based on risk, and every enterprise system has a means for communicating anomalous or exceptional activity.
As a centralized access management platform, SGNL is deeply integrated into applications and services, and continuously evaluates access requests at run-time and based on dynamic policies. In doing so, SGNL has a unique vantage point – able to evaluate access long-after the initial sign-on has been completed at Okta, Entra, or IdPs.
Today’s announcement of Identity Threat Protection is exciting for us at SGNL because of its commitment to standards-based technologies such as CAEP and others in the Shared Signals Framework (SSF) that we believe heavily in and are invested in progressing. For our shared customers, we see this as an amazing opportunity to take insights of anomalous or exceptional activity deep within an application, and have it surfaced during authentication, or re-authentication in the event that anomalous activity warrants session revocation.
With SGNL’s centralized access management, we evaluate each request for access against a set of policies that are defined using dynamic business context from key systems of record. Access requests that are non-compliant with policy are denied, but platform intelligence allows us to evaluate access requests within standard patterns to flag if request patterns seem normal, exceptional, or potentially malicious.
Let’s look at how SGNL + Okta work together to protect your Salesforce data. An Account Executive logging into Salesforce and looking at the accounts in her assigned sector or region, is likely to be assessed as normal and expected activity. If that same Account Executive logs into 3 different systems containing customer data and begins looking at hundreds of records in less than one hour, that may not be expected or normal behavior.
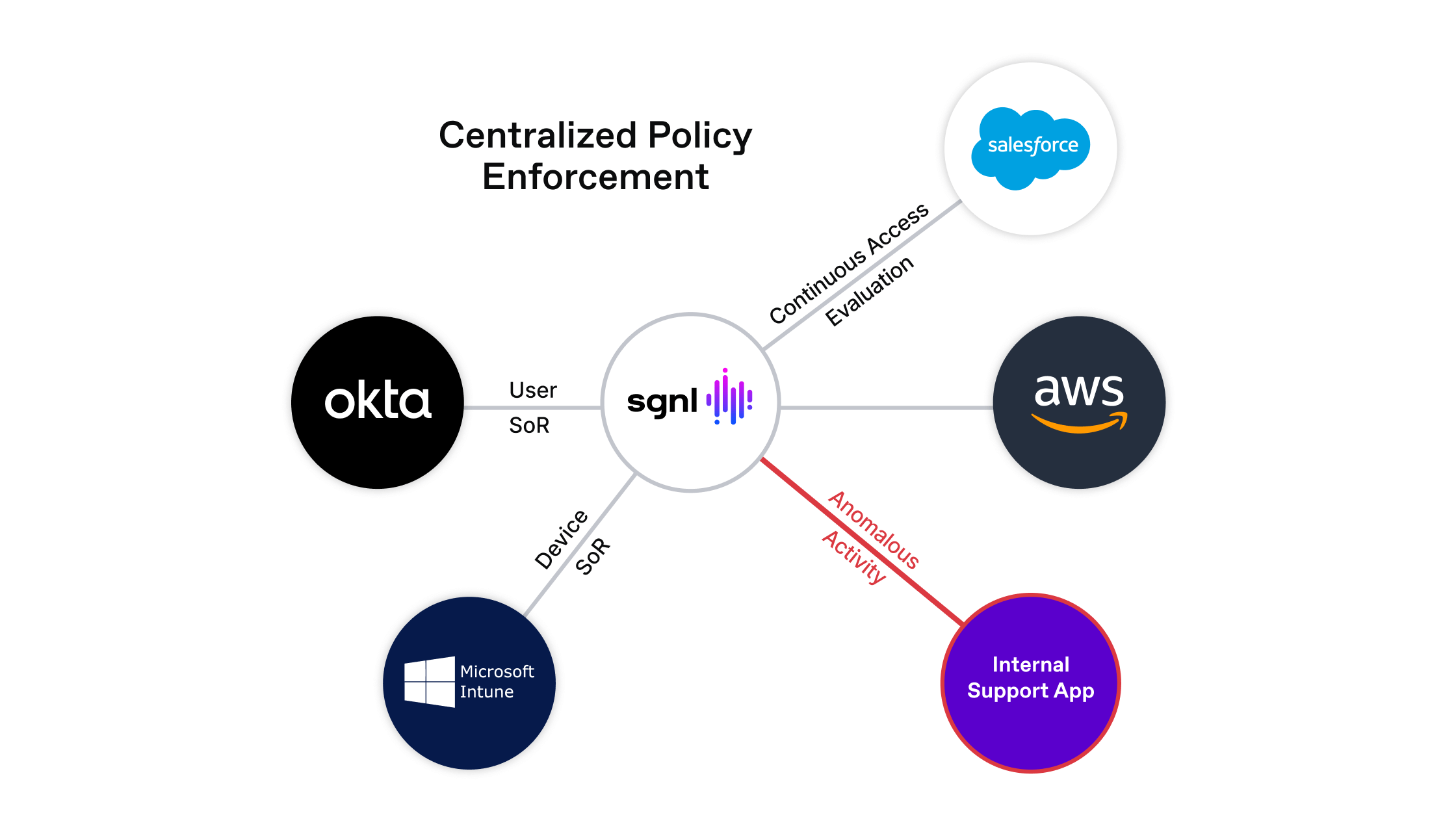
Since SGNL centralizes all access management policies and decisions in one platform, we have a unique vantage point in this scenario and can help proactively protect your landscape using this identity-based intelligence. As the policy engine at the heart of your identity landscape, the SGNL CAEP Hub monitors for anomalies like erroneous AE user behavior in Salesforce. When this anomalous activity is detected, SGNL immediately uses this insight to inform policy access decisions to change how a user’s access decisions are returned, including stopping access from being granted when anomalous activity is detected.
The SGNL CAEP Hub can also notify Okta that something anomalous is occurring. And with SGNL’s pre-built connectors, administrators can notify Okta of the anomalous activity and revoke that user’s session on all applications, forcing them to re-authenticate at Okta as an added layer of security.
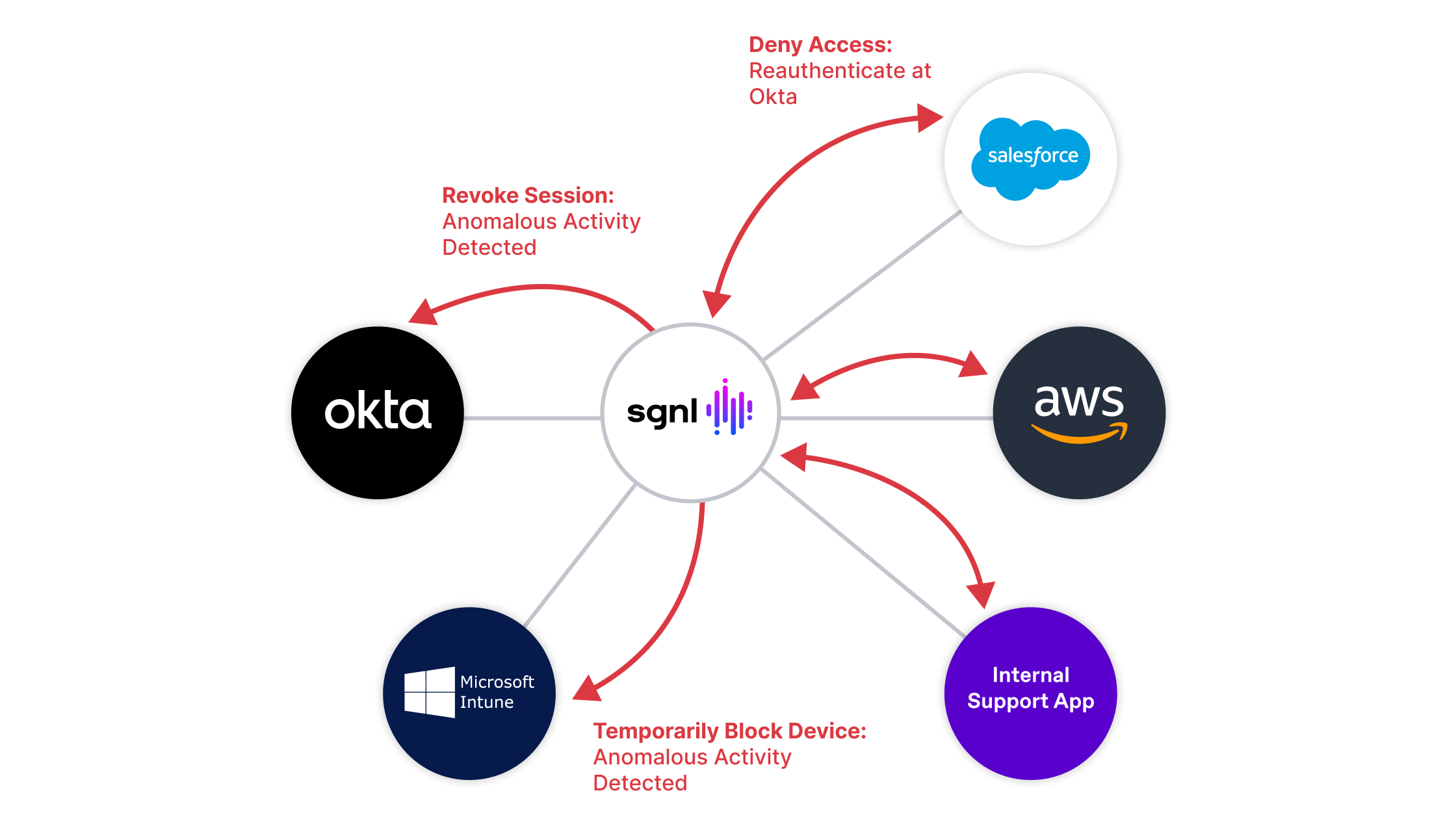
SGNL’s CAEP Hub relies on open standards and open APIs, so that it’s interoperable across the entire heterogeneous ecosystem of your application and security landscape. We balance that with providing simple, out-of-the-box connectors to common applications, services and systems to simplify the process of securing the complete ecosystem with which your workforce identities interact.
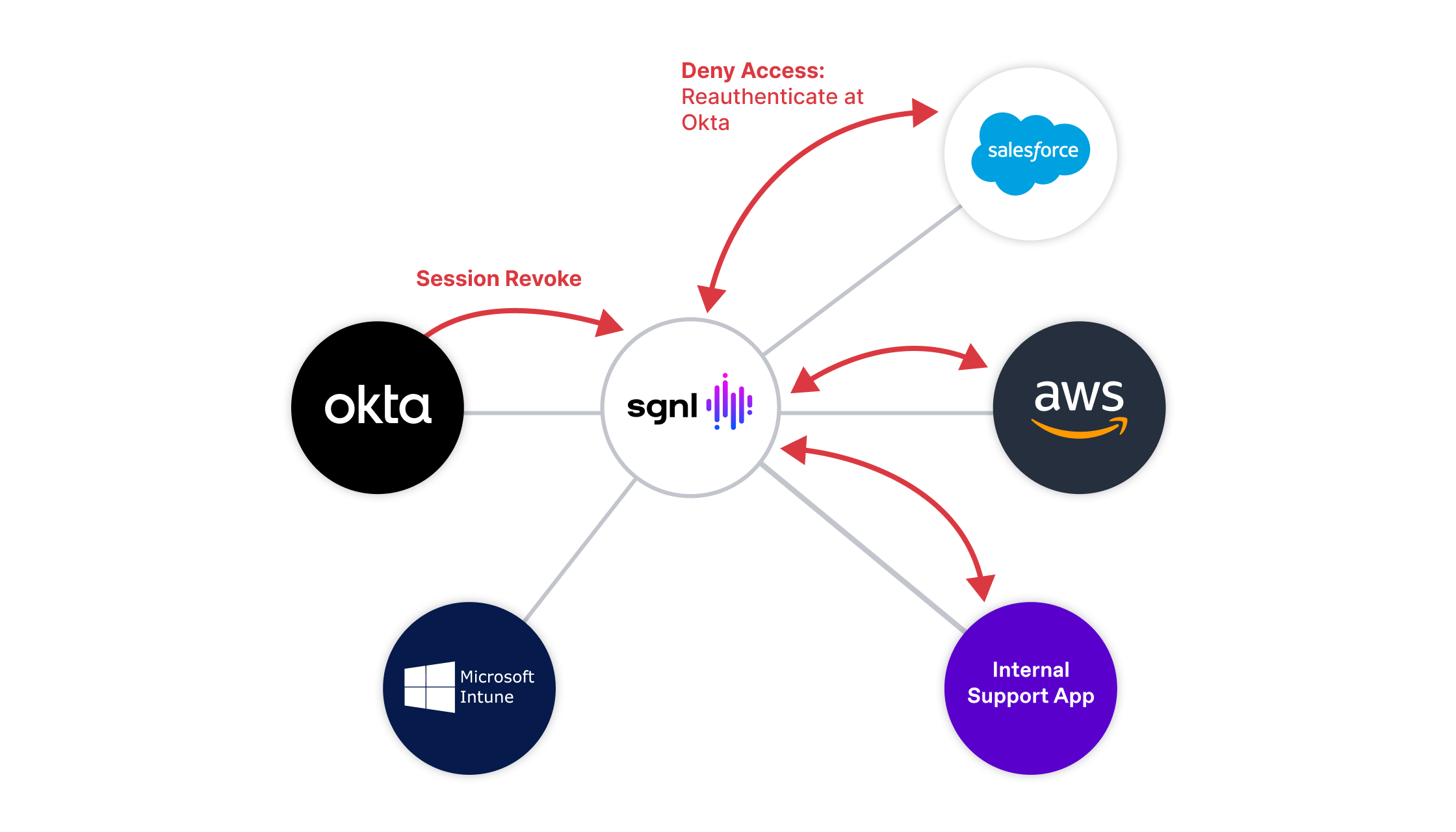
As part of the SGNL and Okta partnership, SGNL also consumes Okta events like Session Revoked or Group Changes to understand changes to identity status. SGNL can immediately take those events and apply the relevant access decisions directly inside of the systems that are connected to SGNL, in real-time.

The continued adoption of standards-based, continuous access management is a huge win for identity teams and their enterprises who are struggling with the challenges associated with static, long-standing access management. It’s also a huge win for end-users, who gain new protections from risk, have fewer sign-in prompts and dynamically gain access with relevant business need.
We believe a SGNL + Okta Identity Threat Detection partnership helps drive adoption of the Continuous Access Evaluation Protocol, which will inherently lead the way for enterprises to achieve identity-centric security, focused on principles of least privilege and zero-trust.
If you’d like to learn more about how SGNL can help you achieve continuous access evaluation and enforcement within your organization request a downloadable version of this blog, see a demo of this use case or schedule time to see SGNL + Okta in action.