The identity space is growing in importance as nearly 80% of cyber attacks on businesses now are based on compromising identities. It remains an evolving area even at an architectural level, as the computing landscape rapidly transitions to the cloud; Organizations are switching to a zero-trust architecture from a “FENCE” (Firewalled Enterprise Network Computing Environment) architecture. In a zero-trust architecture, identity and access management forms the basis of security, and providing leas-privilege access is the goal.
In a zero-trust architecture, identity and access management forms the basis of security, and providing least privilege access is the goal.
As a result, analysts, practitioners and vendors have been catching up on the terminology of various technologies involved. The terms themselves have matured in what they mean to the various constituents.
Areas of Focus
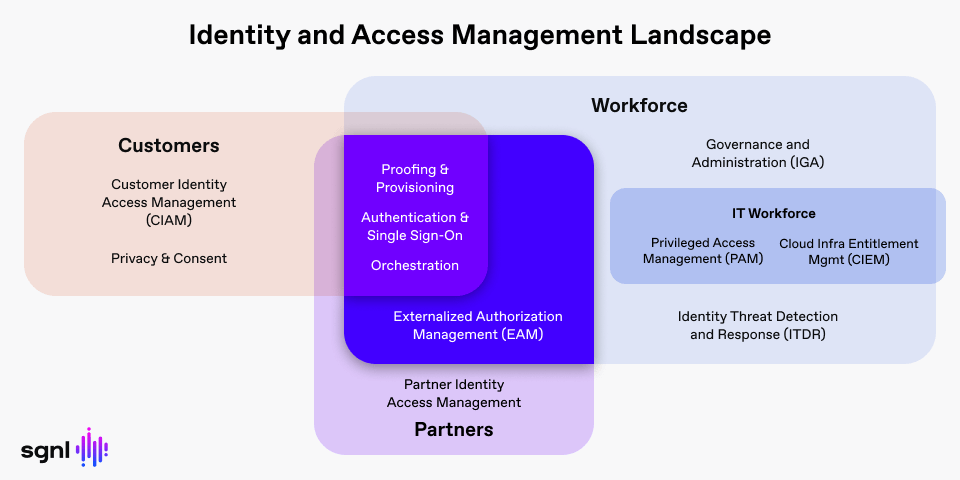
Broadly speaking, there are three constituencies in the identity and access management space:
- Workforce - Relates to an organization’s employees and contractors
- Customers - Relates to an organization’s individual and corporate customers (could be B2B or B2C)
- Partners - Relates to an organization’s partner organizations
The technological requirements of these different constituencies overlap as one might imagine. Since the terminology has evolved, let us look at the individual technologies in the workforce area based on what they do:
Proofing and Provisioning
The technology that manages how real-world credentials are brought into the system and accounts are created and removed fall into this category. The provisioning aspect is sometimes simply called “identity management”.
Verifiable credentials is the latest domain in this area, which bleeds into the broader area of decentralized identities.
Authentication and Single Sign-On
This has been the grand old technology in IAM. In fact, IAM can be synonymous with this in some contexts, or in some vendor and analyst materials.
Authentication, the process by which a user proves their identity in a session, is an active area of work here. It includes new developments like Passkeys and Passwordless Authentication.
Single Sign-On is based on mature federated identity protocols such as SAML and OpenID Connect.
Identity Orchestration
A technology that correlates risk signals from proofing to activity monitoring is typically referred to as simply identity orchestration. It ensures that risk signals generated at various steps of a user’s journey are not siloed. Collective use of such signals is important to generate an accurate risk assessment of any user account.
Externalized Authorization Management (EAM)
EAM is a relatively new area, where access decisions which were previously hidden inside applications are now delegated to a separate (i.e. external) technology component. This typically results in fine-grained access control, and is crucial to the security of a zero-trust architecture. This is because an overly permissive environment enables attackers who pose as insiders to get broad privileges and do a lot of damage. With fine-grained access control, organizations can effectively limit the “blast radius” in case of a breach. SGNL is a key vendor in this space, with our innovative Just-In-Time Access Management platform.
Fine-grained access control is crucial to the security of a zero-trust architecture. This is because an overly permissive environment enables attackers who pose as insiders to get broad privileges and do a lot of damage. With fine-grained access control, organizations can effectively limit the “blast radius” in case of a breach.
Governance and Administration
Ensuring that user accounts are provisioned with proper role and entitlement information in various systems is covered by this technology (IGA). It includes initial provisioning as well as its maintenance (e.g. joiners, movers, leavers management, or activities such as certifying access of existing users).
This is an area where the terminology seems to be evolving. Until recently, the IGA space was seen as a separate area of technology from an analyst point of view. In our discussions with customers, we have discovered that this is often thought of by customers as just “Access Management”. Since the single sign-on portion used to be called (or still is called) “Access Management”, there appears to be a terminology conflict here.
In terms of product capabilities, major vendors in the Authentication and Single Sign-On space now also offer comprehensive IGA features within the same products, so the combined products are sometimes thought of as “Access Management” products.
Major vendors in the Authentication and Single Sign-On space now also offer comprehensive IGA features within the same products, so the combined products are sometimes thought of as “Access Management” products.
Identity Threat Detection and Response (ITDR)
Since identities are critical to zero-trust architectures, and most attacks are now based on compromised identities, it is important to quickly detect threats by intelligently analyzing various sources of truth such as logs and alerts from SIEM (Security Incident and Event Management), Identity Orchestration, XDR (Extended Detection and Response). ITDR not only does this, but also analyzes who has privileged access, how various services are configured and what are the known vulnerabilities that have not been patched, to ascertain potential threats. It then responds by either revoking user access and remedying the situation or reporting / alerting about the issue.
Areas Specific to IT Administrators
Some users in an organization’s IT department require uniquely powerful access to critical infrastructure systems. As a result, this is a specialized area of work that ensures such powerful access is kept highly secure, even if it requires cumbersome user interfaces or the use of physical keys to access such infrastructure. Both the technologies described below contain “secret management” capabilities, which are sometimes thought of as a separate technology area.
Privileged Access Management
Privileged accounts of SaaS systems or internal systems require special care. Sometimes shared accounts are required by these systems, and the password may need to be shared with multiple users in an organization. The Privileged Access Management systems ensure the security of individual or shared accounts through vaulting and password rotation.
Cloud Infrastructure Entitlement Management
This is a relatively new area of work, with many vendor products enabling users to gain privileged access to cloud infrastructure systems. This technology has similarities with the PAM technologies above as well as the IGA technologies described earlier. SGNL’s AWS solution provides an innovative just-in-time approach to ensuring tight security of Cloud Infrastructure Entitlements