
RBAC and ABAC cannot contain privilege sprawl, and in fact contribute to it. Dynamic authorization based on signals and data from across an enterprise can bring us closer to a “least privilege” access model.
Whether they are creating software or shoes, data is the operational backbone of the modern enterprise. Access to high quality data at the right time, by the right people, has been proven to provide a huge competitive advantage.
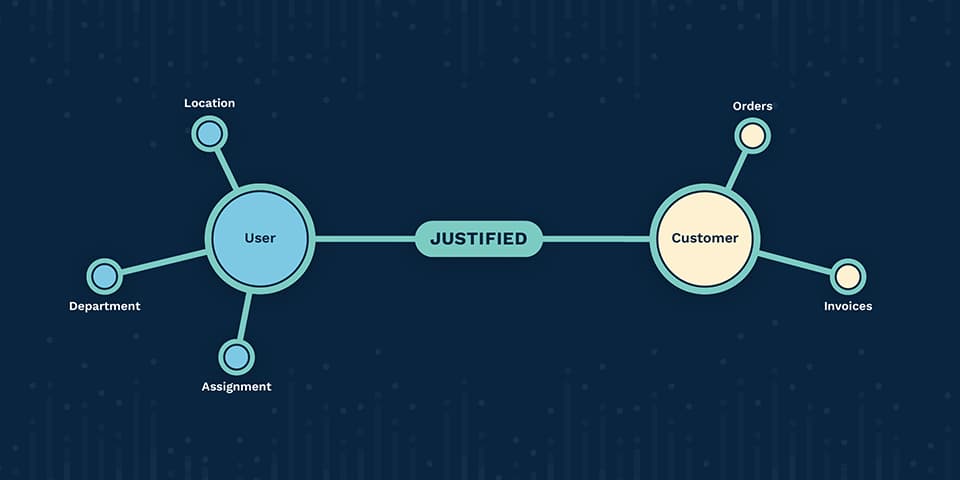
The focus on data increases its value - making it one of the most valuable assets in an organization. As such, a disciplined approach is required to ensure it is well-protected. At SGNL we believe the future of managing access to this data is through a strategy that encompasses business justification, or Justified Access.
For decades, protecting data stored in computer systems has meant the configuration of static access control lists (ACLs) and access control entries (ACEs) based on who has access, what they have access to, and what they can do with that access. As time has passed, organizations and products have also gotten more and more clever about how to describe who can get that access. The industry at large has explored roles as a means of grouping similar users and granting access (via Role Based Access Control or RBAC). More recently, there’s been a realization that almost any attribute (or group of attributes) can establish a population of users that might have similar data access needs (via Attribute Based Access Control or ABAC).
These strategies have gone a long way to granting the workforce access to the data they need to do their job. People who have a Customer Success Manager title (for example) might need to access customer data to provide support, issue refunds, update records, or tens of other possible actions depending on the business. Similarly, users in Sales and Support departments might need to understand telemetry to provide insights to their customers and prospects as well as in forecasting, budgeting, or churn analysis.
There are several downsides to Role and Attribute-based Access Control:
For a more in-depth discussion, check out What Ails Enterprise Authorization by our CTO, Atul Tulshibagwale
One not-so-obvious downside of Role and Attribute-based access control is that it glosses over the question of whether a user should access a specific piece of data at a specific point in time with some business justification. RBAC/ABAC methodologies deal solely in whether a user can access a specific piece of data which often leads to a massive breadth of ambient access for every user.
For many organizations, whether a user should be utilizing their privilege to access data is documented in privacy and security training, organizational policies, and retroactively in security/compliance audits - not when data access is actually happening.
As you might suspect, this causes an array of challenges for different parts of an organization:
At SGNL we’ve seen these downsides and symptoms manifest at organizations both large and small and believe the solution lies in a new, principled type of Justified Access management strategy:
At SGNL we’re creating the future of Justified Access management, delivering an authorization solution that determines who should be able to access data based on their current task, business need, and justification, sourced from the organizational context that exists in the systems your organization already manages.