It was awesome to meet fellow implementers, Gartner analysts and attendees interested in CAEP at the first ever CAEP Interoperability Event (CAEPIE), held at the Gartner IAM Summit in London on March 4th and 5th, 2024. This was the culmination of many weeks of work put in by implementers from various large and small companies with the immense support of Felix Gaeghtgens and Erik Wahlstrōm of Gartner.
Here are some of my biggest takeaways and key conversations had during the event:
CAEP’s momentum and path forward
CAEP solves a fundamental problem that zero-trust architectures struggle with: Every access needs to be evaluated independently, but the latest data available to make those decisions isn’t available at the point where the evaluation needs to take place. Specifically, today information about session hijacking, device compliance or credential changes are siloed and cannot be shared even though they are critical to session security.
The attendees clearly saw the value of CAEP. They saw how CAEP can be added to existing services like IdPs, SaaS services, IGA services and others. They saw how relevant information from each of these services could be propagated using CAEP events such as session revocation, credentials change and token claims change can be used to dramatically improve security at all other services that share the same users. The SGNL CAEP Hub caught the users’ imagination by seeing how easy it made getting CAEP enabled, writing and enforcing rules for event processing and covering the “last mile”. Where systems don’t yet support CAEP, products like SGNL’s CAEP Hub are able to use proprietary APIs of those systems to cover the “last mile”.
There were a total of 8 implementations participating in the CAEP interoperability event. Six of those were available on-site for attendees to take a closer look at, and 2 had participated remotely in the run up to the conference and achieved interoperability. The implementations that successfully demonstrated interoperability are: Okta, Cisco Duo, Cisco Webex, SGNL, SailPoint, Helisoft, VeriClouds and SGNL’s non-commercial implementation, caep.dev. See the interoperability matrix below that shows the result of the CAEPIE:
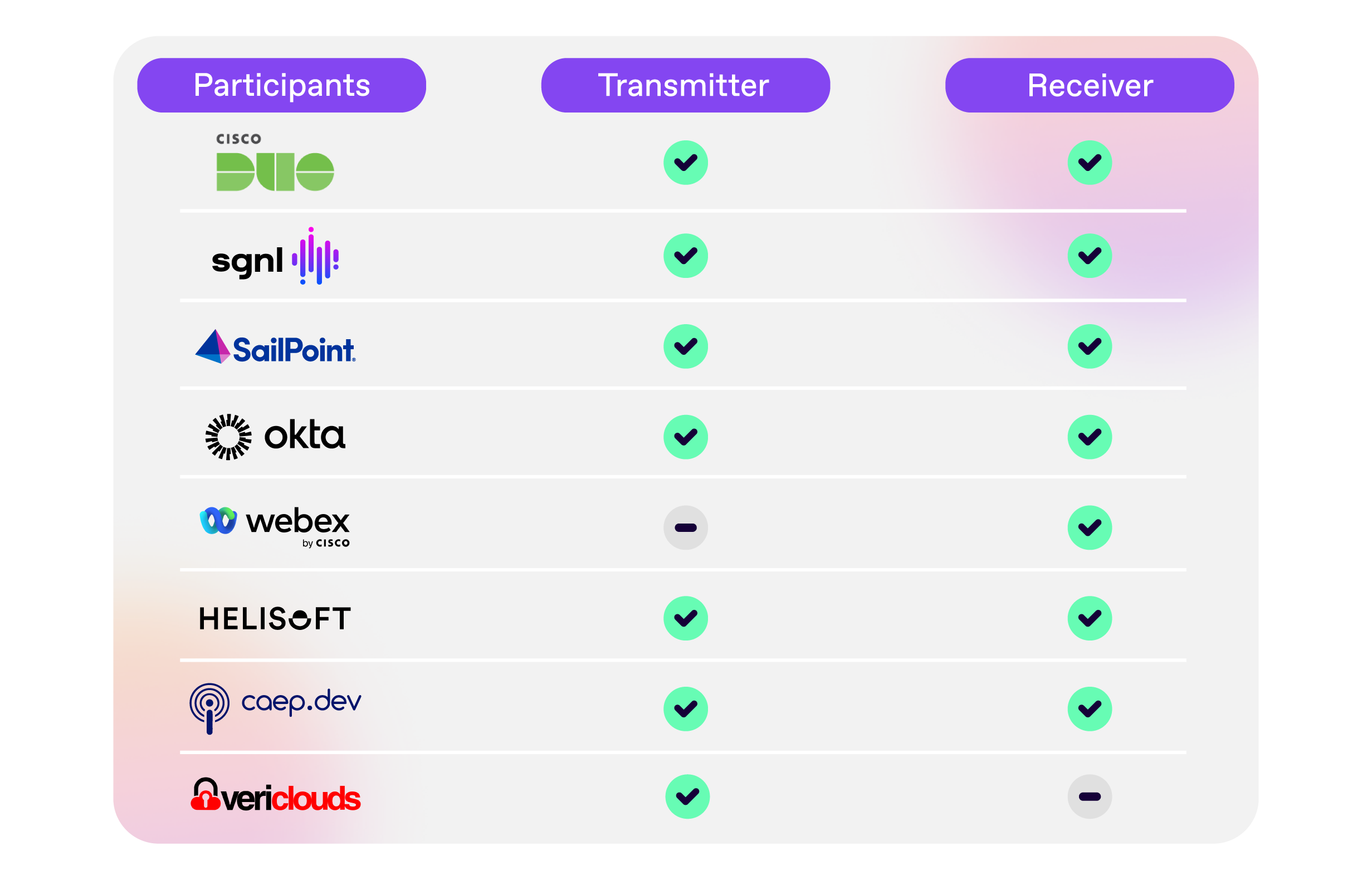
I look forward to more implementers participating in future such events, and while a venue for the next event hasn’t been formalized yet, there is definite interest in repeating this later this year - both from conference organizers and from additional implementers who didn’t get a chance to participate in this one.
Other Key Takeaways
1. Rallying around outcome driven metrics
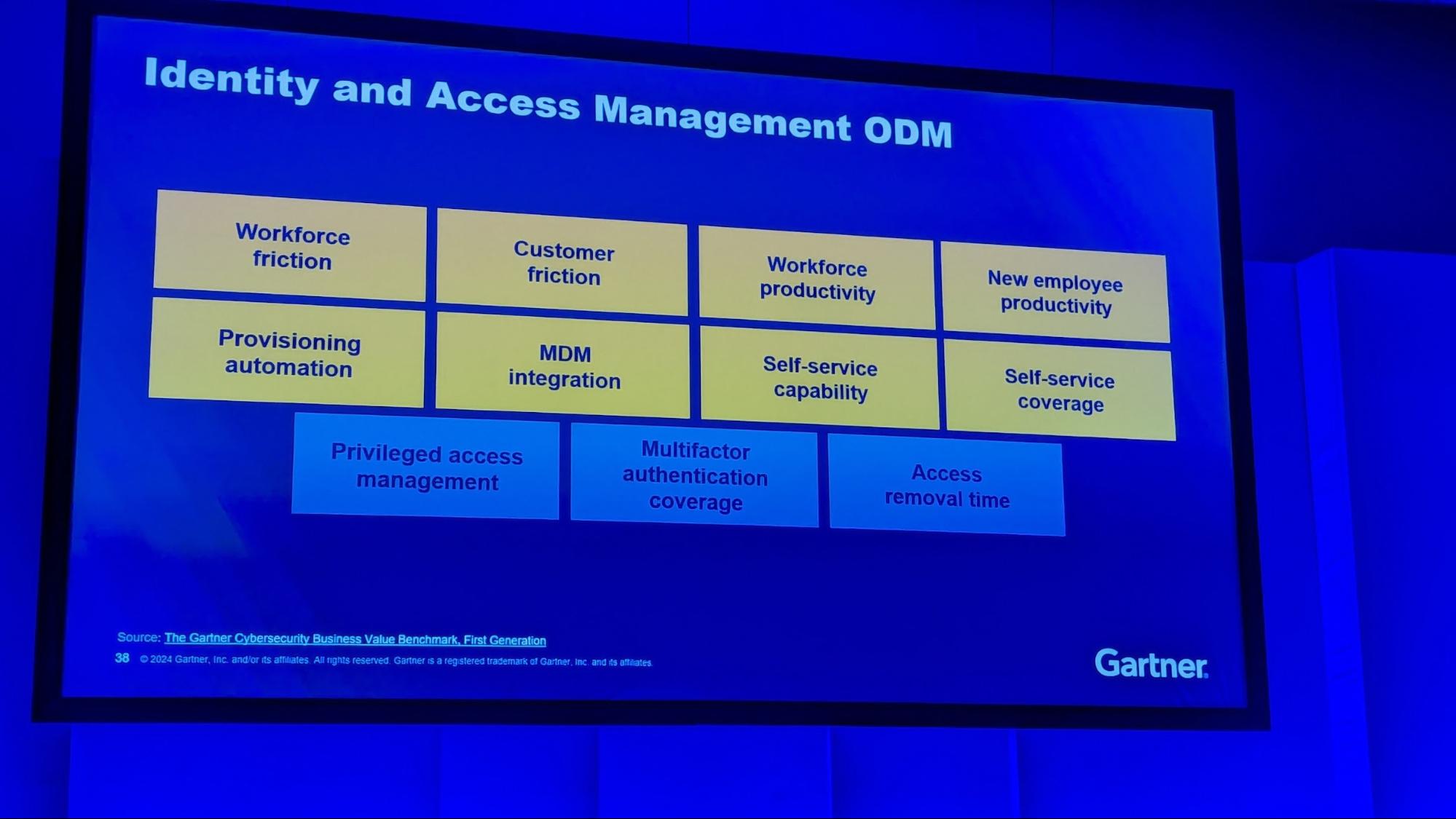
Paul Proctor’s opening keynote was very insightful and well received. What struck me was how the shift towards outcome-driven metrics within the identity and security domains could transform the internal conversation about cybersecurity budgets into a practical tradeoff between budget and “Protection Level Agreement”. It’s a given that breaches can occur, hence, the focus is on preparing not just technologically but also from a business perspective. Metrics that align with business outcomes (i.e. Outcome Driven Metrics or ODM), such as the speed of access removal and the reduction in potential breach impacts, are a great way to think about this. These metrics serve as a gauge for an organization’s security posture, providing board-level insights into the effectiveness of identity management strategies.
2. Zero Trust is all about authorization
Jan Herrmann’s talk on Siemens’ Zero Trust implementation was another memorable one, with an emphasis on its application to authorization processes, and how its success truly centralizes around authorization. In his presentation, Jan detailed their approach to Zero Trust, highlighting the prioritization of authorization as a central strategy. Zero Trust is seen as a journey, with achievable milestones and practices that can be implemented immediately, including many examples within Siemens’ environment that they shared in the graphics below.


A key point he made was: attributes need to be shared across systems to determine access trust. This is a foundational principle of Zero Trust, and one which can be achieved using CAEP.
3. CAEP enablement doesn’t have to wait on your existing systems

Lastly, the agility of CAEP enablement strategies was a key takeaway - and the fact that existing systems’ CAEP adoption doesn’t need to slow enterprises down. SGNL’s CAEP Hub was spotlighted as a groundbreaking solution, acting as a bridge for policy communication across systems, regardless of their native CAEP support. With CAEP Hub, SGNL is now acting as the Rosetta Stone to receive and transmit signals across your existing critical systems, even if they themselves do not yet support CAEP. This represents a major step forward, offering immediate benefits by enhancing protection for critical systems and sensitive data. The enthusiasm around CAEP Hub underscored the industry’s eagerness to adopt technologies that can offer immediate security improvements, even as broader support for CAEP continues to develop. Learn more about CAEP Hub in the announcement here.
The Gartner IAM Summit in London proved to be a rich source of insights and trends for identity professionals. From the crucial role of outcome-driven metrics in aligning security efforts with business objectives, through the nuanced understanding and implementation of Zero Trust, to the innovative strategies for CAEP enablement, it’s clear that the field is evolving rapidly. As we continue to navigate these changes, we need to emphasize practical, immediate solutions that can be implemented alongside long-term strategies for security and identity management. The discussions and presentations at the summit have undoubtedly set the tone for the priorities and directions that will shape the identity security landscape in the coming year.
See you at the Gartner IAM Summit in Texas this Fall!

